Group Policy Objects
What is a Group policy object? A virtual group of policy settings is called a Group Policy Object (GPO). A GPO has a distinctive name, like a GUID (globally unique

Active Directory Password Policy
How to Configure a Password Policy – An Overview & Guide Password Policy ensures that a user password is strong and is changed in a periodic manner so that it
Desktop shortcuts using AD Group Policy: The complete guide
Active Directory (AD) Group Policy Objects (GPOs) are used to centrally manage user account settings, system configurations, and access to network resources. Here are some of the important benefits of
How to configure the scheduled scan in Windows Defender via GPO
In the dynamic landscape of cybersecurity, ensuring regular system scans for threats is crucial. For system administrators managing a network of Windows devices, configuring scheduled scans in Windows Defender through
Configure UAC Behaviour for Admin Approval Mode via GPO
User Account Control (UAC) is a fundamental security feature in Windows environments. It helps mitigate the impact of malware by requiring approval for changes to the system, even when made
GPO to prevent regular users from changing MSI installation options
In a managed IT environment, ensuring the consistency and security of software installations is essential. Allowing regular users to change installation options during the installation of an MSI package can

Delegating OU permissions with minimal risk: the expert’s comparison guide
Short definition: Active Directory OU delegation is granting scoped, task-specific permissions on Organizational Units (OUs) to security groups—without domain-wide admin rights—so teams can safely manage only what they must. Why
Group cleanup scripts with usage analysis
Active Directory group sprawl is not just “messy directory hygiene”—it directly affects access risk, troubleshooting time, audit outcomes, and even authentication performance at scale. The hard part isn’t deleting
How to design nested groups for application access control
<!doctype html> Nested groups are one of the most powerful (and most misunderstood) primitives in Active Directory access control. When designed well, they let you express business intent once and
Build departmental OU structures for decentralization
<!doctype html> Decentralizing administration in Active Directory (AD) is usually not a political decision—it’s an operational necessity. As environments grow, central IT becomes the bottleneck for everyday tasks: onboarding, group
SIEM alert rules for AD exploitation attempts
SIEM Alert Rules for Active Directory Exploitation Attempts SIEM Alert Rules for Active Directory Exploitation Attempts If you’re monitoring Active Directory with a SIEM, your job isn’t “collect all the
Managing GPOs in Active Directory
What you will learn: Managing an Active Directory (AD) network can become a little cumbersome once the number of resources in the network becomes larger. There is a myriad of
Active Directory Account Lockout Policy
What is an Account Lockout Policy? An account lockout policy is a built-in security policy that allows administrators to determine when and for how long a user account should be
How to delegate permissions to create GPOs in Windows
Group Policy is a feature in Windows that provides centralized management and configuration of operating systems, applications, and users’ settings in an Active Directory environment. Delegating permissions to create GPOs
How to create GPO to schedule security intelligence updates for Windows Defender
In the ever-evolving landscape of cybersecurity, staying ahead of threats means regularly updating security intelligence. For Windows environments, this is particularly true for Windows Defender, Microsoft’s integrated antivirus and anti-malware
Automatically deny elevation requests from standard users via GPO
In enterprise environments, maintaining strict control over user privileges is key to ensuring network security and operational efficiency. One aspect of this is managing elevation requests – particularly, automatically denying

Block windows app installation with elevated privileges using GPO
In an enterprise IT environment, controlling the permissions and actions of the Windows Installer is crucial for maintaining security and consistency. Allowing the Windows Installer to use elevated permissions during
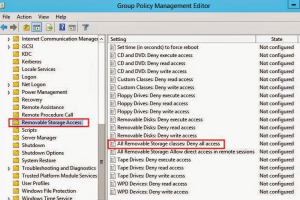
Disabling USB ports using Group Policy: An expert guide
Short version (for snippets): To block USB storage with Group Policy, open gpmc.msc, create a new GPO, then enable Computer Configuration > Policies > Administrative Templates > System > Removable
Tools for visualizing OU and group structures
Tools for visualizing OU and group structures Active Directory gets difficult to reason about long before it gets “big.” A few years of organic growth—new teams, acquisitions, hybrid identity, app-specific
Using groups for access to shared drives and resources
Shared drives and file shares look simple on the surface: “give Finance access to \FS1Finance.” In reality, they become one of the fastest-growing sources of permission sprawl, audit pain, and
Use Protected Groups for critical OU containment
“OU containment” is supposed to be your safety boundary: admins can manage what’s inside an OU, but they can’t casually reach outside it. In real Active Directory environments, that
Local Group Policy Editor
Group Policy in Active Directory (AD) simplifies the administrative burden and makes management a whole lot easier. When an administrator needs to control and configure settings on a local computer
Windows Group Policy Object Inheritance: Explained
Introduction: In Active Directory (AD), there is a significant feature called Group Policy that allows you to implement specific settings for users and computers. Administrators can apply hundreds of different
Fine-Grained Password Policy: A Step-by-Step Configuration Guide
Microsoft has two solutions for deploying the requirements for Active Directory domain users’ passwords. The requirements, referred to as the password policy, can be deployed through Group Policy Objects (GPOs)
How to disable basic authentication for WinRM Service using GPO
In the realm of Windows systems administration, securing communication channels is a critical task. One key aspect of this is configuring the Windows Remote Management (WinRM) service, which allows for
How to block Windows Spotlight using GPO
Windows Spotlight is a feature in Windows 10 and later versions that displays different backgrounds on the lock screen and offers suggestions on the lock screen. While it can be
GPO to detect application installations and prompt for Elevation
In an enterprise environment, controlling software installation is vital to maintain system integrity, security, and compliance. Group Policy in Windows provides a powerful way to manage this. One effective approach
DNS delegation architectures for multi-forest environments
Architecture • DNS • Active Directory If you run more than one Active Directory forest, DNS is the fabric that lets users, apps, and domain controllers in one forest reliably
Maintaining OU consistency in hybrid environments
Hybrid identity is supposed to feel like one system: the same users, the same groups, the same access decisions—just stretched acrosson-premises Active Directory and cloud identity. The reality is that
Mapping users to OUs via dynamic properties
Active Directory (AD) works best when Organizational Units (OUs) reflect how you operate: how you delegate, how you apply policy, and how you lifecycle identities. The problem is that
How to lock down OU movement and deletions
Organizational Units (OUs) are more than “folders” in Active Directory. They’re policy boundaries (GPO linking), delegation boundaries (who can manage what), and often the backbone of your administrative model.
How to enforce policy changes with minimal topology disruption
Enforcing policy changes with minimal topology disruption In Active Directory, “policy change” usually means Group Policy, security baselines, authentication hardening, and configuration shifts that must apply consistently. “Topology disruption” is

Managing GPOs with Group Policy Management Console
Group Policy Management Console: An Introduction The Group Policy Management Console (GPMC) is a one-stop solution for performing all the Group Policy functions an administrator has to deal with. This
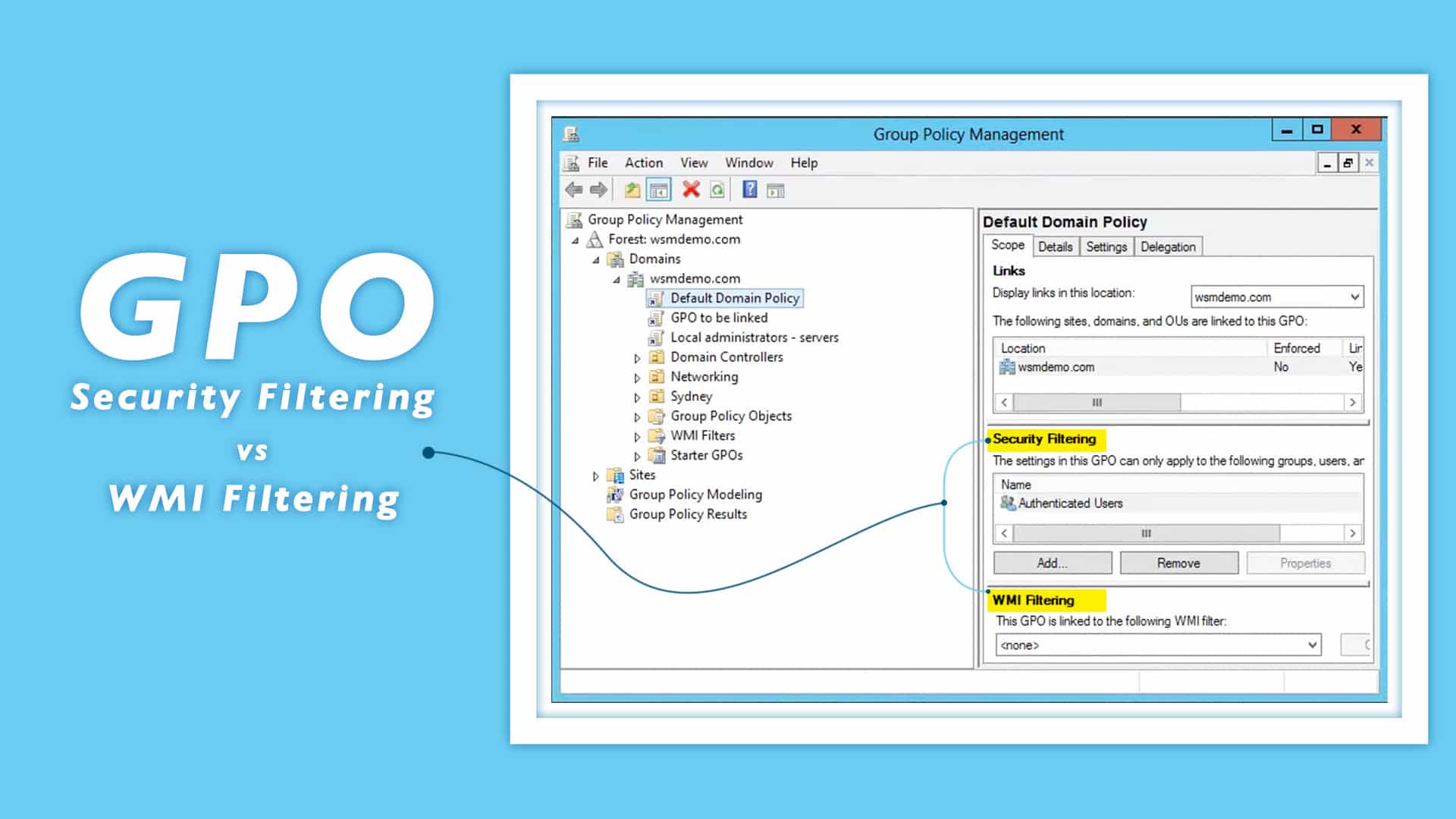
GPO security filtering and WMI filtering: An explanation
What you will learn: GPO security filtering vs WMI filtering – where to apply what? Fret not, let’s take a step back. Group Policies can be assigned at the OU,
Group Policy Management Console (GPMC) – Part II
In part I of Group Policy Management Console (GPMC), we introduced the GPMC MMC snap-in, its functionalities and also looked at how to perform a few basic tasks. In this part, we
How to disable notifications for blocked programs in Windows Firewall via GPO
In a managed IT environment, controlling how users interact with security alerts is crucial for maintaining operational efficiency and security. One such aspect is managing notifications from the Windows Firewall,
How to enable Windows Defender to analyze mail bodies and attachments via group policy
In an era where email remains a primary vector for cybersecurity threats, it’s crucial for system administrators to ensure that all possible precautions are taken to protect networked systems. One
GPO to prevent sending unencrypted passwords to Third-Party SMB Servers
In a networked environment, especially in enterprise settings, safeguarding sensitive data, including passwords, is a critical aspect of cybersecurity. One significant risk is the transmission of unencrypted passwords to third-party
Transitioning AD schema versions safely: runbook & pitfalls
Active Directory The schema is your forest’s data contract. When you raise its version—via adprep or app extensions—you change what can exist and how it behaves. This self-contained guide explains
Recovering deleted groups from Recycle Bin
Recovering deleted groups from Recycle Bin Deleting the wrong group in Active Directory is one of those mistakes that feels small until everything attached to it (file shares, application roles,
AD group expiration and recertification best practices
<!doctype html> Active Directory groups are one of the most powerful—and most quietly dangerous—access control primitives in Windows environments. They’re easy to create, easy to nest, and easy to forget.
How to use scripts to compare group memberships
Comparing group memberships sounds simple until you hit real-world friction: nested groups, mixed sources of truth, inconsistent naming, timing issues between DCs, and “who changed what” questions that appear

Role-based access control (RBAC) in Azure
Azure RBAC is the authorization system used to control who can do what across Azure resources. It is designed to keep access granular, auditable, and aligned to real operational responsibilities—without
Active Directory Policies
The time and cost spent to organize, control, and maintain the IT infrastructure of an organization are very high. It is the IT administrator’s job to ensure that the employees
GPO Delegation
Introduction : Group Policy helps administrators with centralized control and configuration of user settings, operating systems, and applications. A Group Policy Object (GPO) is a collection of Group Policy settings that
How to map network drives with Group Policy
How to map network drives with Group Policy In earlier days, system administrators relied only on logon scripts to map networking drives, a complex and time-consuming process. To eradicate these
How to block connection to non-domain networks via GPO
In the landscape of enterprise IT management, securing network connections is a top priority. One aspect of this is preventing domain-joined computers from connecting to non-domain networks, which can be
How to prevent users override certificate errors on Microsoft Edge using GPO
In the management of an enterprise IT environment, ensuring secure web browsing is crucial. One aspect of this is managing how users interact with security warnings, especially those related to
Restrict anonymous access to Shares and Named pipes via GPO
In networked environments, especially in enterprise settings, securing communication channels and shared resources is crucial for maintaining data integrity and privacy. A critical aspect of this security is to prevent

AD high-availability: RODCs and cross-site redundancy
Active Directory high availability Design for the worst day: local logons at branch speed, safe failover by intent—not accident. RODC Sites & Services Next Closest Site Password Replication Policy Definition
How to sync AD groups to cloud services securely
Syncing Active Directory (AD) groups to cloud services sounds simple: “make the same groups appear in the cloud.” In practice, it’s one of the easiest ways to accidentally leak
Using groups for licensing control in Microsoft 365
If you’re still assigning Microsoft 365 licenses user-by-user, you’re doing identity operations the hard way. Group-based licensing flips the model: instead of asking “What does Alice need?”, you decide “What
How to export group membership lists with PowerShell
Exporting group membership seems simple until you try to do it in a real environment: nested groups, thousands of members, mixed object types (users, computers, service accounts, contacts),
Detecting Pass-the-Hash attacks
Pass-the-Hash (PtH) is a credential abuse technique where an attacker uses a captured NTLM password hash to authenticate to other systems—without ever knowing the user’s plaintext password. In an Active
Active Directory Group Policy
Introduction- What is Group Policy? Group Policy is a security tool built into Microsoft Active Directory that gives network administrators access to a variety of advanced settings. Administrators can set
Group Policy Results
What are Group Policy Results? System administrators have a tough time determining what settings are actually being applied to users and computers because there may be several GPOs linked at
How to change the NTFS and share permissions
New Technology File System (NTFS) is the standard file management system provided by Microsoft. Access to any data stored in the NTFS is governed by NTFS permissions. Share permissions govern access to folders shared over a network. It’s not possible to modify permissions for the subfolders or objects in a particular share because these permissions are commonly applied to all its files and folders. Watch this video where we show how you can change the NTFS and share permissions.
Check out a more detailed explanation in our article here 👇
https://www.windows-active-directory.com/managing-shared-resources.html
For more such articles on managing shared resources, visit our website 👇
https://www.windows-active-directory.com/
To stay updated about industry trends and Active Directory best practices, subscribe to our monthly newsletter👇
https://www.manageengine.com/active-directory-360/iamroundup-newsletter.html
#NTFS #shared #windows #activedirectory
How to block automatic connection to Wi-Fi Hotspots using GPO
For organizations managing a fleet of Windows devices, ensuring secure and controlled network access is paramount. One aspect of this is preventing devices from automatically connecting to potentially unsecured Wi-Fi
GPO to block unverified downloads on Microsoft Edge
In today’s digital landscape, one of the key challenges for system administrators is securing web browsers against potentially harmful downloads. Microsoft Edge, a widely used browser in corporate environments, allows
How to deny anonymous enumeration of SAM accounts using GPO
For system administrators, safeguarding sensitive account information within the Windows environment is crucial. One important aspect of this is preventing the anonymous enumeration of Security Account Manager (SAM) accounts. Unauthorized
SID filtering in complex AD layouts: the one-bit boundary that decides what crosses your forest
Quick definition: SID filtering is a trust-side control that removes foreign SIDs—including values in SIDHistory—from a user’s authorization data as it traverses a trust. It prevents privilege escalation by honoring

Understanding group nesting limits and token size
<!doctype html> Group nesting is one of Active Directory’s most powerful features: you can model roles and access using a few reusable groups, then compose them into higher-level “business” groups.
Role-based access control (RBAC) using AD groups
Role-based access control (RBAC) is the idea that people don’t get permissions because of who they are, but because of what they do. In Windows environments, Active Directory (AD)
How to detect circular group nesting and resolving token bloat
Group nesting is one of Active Directory’s most powerful features: it lets you express roles, aggregate access, and scale delegation without touching every user object. It’s also one of
Monitoring Group Policy for backdoors
Monitoring Group Policy for Backdoors (GPO Tampering Detection & Response) Group Policy is one of the most powerful configuration channels in Active Directory—and that’s exactly why attackers love it. If
Group Policy Objects (GPOs): Different Policy Settings
Introduction Group Policy includes policy settings that affect both users and computers. The settings under Computer Configuration control how the computer is configured. The settings under User Configuration control the
How to force Group Policy update?
What you will learn from this article: Group Policies are a set of security and management instructions that are administered and updated to ensure secure and smooth operations of an
HOW TO DEPLOY EXE FILES USING GPO
Group Policy is an hierarchical infrastructure in Microsoft’s Active Directory which provides a centralized means for a network or system administrators to configure Windows servers and desktops. A virtual collection of policies constitute
How to disable JavaScript in Adobe Reader DC using GPO
For system administrators managing a network of computers with Adobe Reader DC, it’s essential to maintain security and control over the software configurations. One such critical setting is the management
GPO to block malicious site access on Microsoft Edge
In a digital landscape where web-based threats are constantly evolving, securing the web browsing experience is a top priority for system administrators. Microsoft Edge, being a commonly used browser in
Prevent remote logon for local accounts with blank password – GPO
In the realm of network security, one critical aspect is ensuring that all accounts, especially those with remote logon capabilities, are secured with strong passwords. Allowing remote logon for local

Automating inactive user account cleanup: beyond “run a script every 90 days”
A production-grade playbook for hybrid Active Directory and Microsoft Entra ID (Azure AD) inactive user account cleanup: signals, staged actions, reversibility, and governance—backed by copy‑paste runbooks. On this page Quick
How to detect privileged group membership changes
Privileged group membership is one of the highest-leverage control points in Active Directory. If an attacker can add an account (or a computer, service principal, or nested group) to
How to secure OU and group changes with audit trails
<!doctype html> Organizational Units (OUs) and security groups are two of the most powerful “control surfaces” in Active Directory. OUs decide where objects live, what policies apply, who can administer
Managing dynamic distribution groups in AD
“Dynamic distribution groups” sound like an Active Directory feature, but they’re really an Exchange feature that stores a group object in AD and uses recipient filtering to decide who
Detecting unauthorized domain replication
Unauthorized domain replication is one of the fastest ways for an attacker to turn “some access” into “total access.” If someone can trigger directory replication (or abuse replication rights) they
Active Directory Group Policy in a Nutshell
What you will learn: Managing an Active Directory (AD) network can become a little cumbersome once the number of resources in the network becomes larger. There is a myriad of
Active Directory Account Policy
What you will learn: Active Directory has a strong authentication mechanism such as the Kerberos authentication mechanism, that prevents malicious intruders from gaining access to resources within the network. However,

How to demote a Domain Controller: A step-by-step guide
Are you a Windows system administrator looking for how to demote Domain Controller in your Active Directory? You have landed on the right place. There are many reasons to demote a
How to disable flash on Adobe Reader using GPO
In a networked environment, managing software configurations centrally is crucial for maintaining system security and performance. For system administrators, one task in this realm is disabling Flash in Adobe Reader
Configuring Windows Defender Network Protection via Group Policy
In an increasingly interconnected world, network security is paramount for any organization. Windows Defender Network Protection is a critical feature that helps prevent employees from accessing dangerous domains that might
GPO to prevent autoplay on non-volume devices
Autoplay is a feature in Windows that automatically executes a predefined action when a new device, such as a USB drive, camera, or phone, is connected to the system. While

Auditing Nested Group Memberships: An Expert Guide
Reading time: ~14–18 min • Last updated: 2025-09-29 Nested groups are convenient, flexible, and dangerously opaque. This guide shows how to audit them properly in Active Directory and
Delegation wizard: common use cases and pitfalls
The Delegation of Control Wizard in Active Directory Users and Computers (ADUC) looks deceptively simple: pick an OU, pick a group, tick a few boxes, and suddenly the helpdesk
How to use OU structure to mirror organizational hierarchy
Organizational Units (OUs) feel like the “obvious” place to represent how a company is shaped: divisions, departments, regions, and teams. In Active Directory, that instinct is half right and
Best practices for naming conventions in group management
Group sprawl is rarely caused by “too many groups” alone. It’s usually caused by groups that are hard to interpret, hard to search, and easy to misuse. A consistent
How to track rogue domain controllers
Tracking Rogue Domain Controllers in Active Directory (Detection + Response Playbook) A rogue domain controller (DC) is any system that is acting as a DC or participating in DC trust/replication

