How to Configure a Password Policy – An Overview & Guide
Password Policy ensures that a user password is strong and is changed in a periodic manner so that it becomes highly impossible for an attacker to crack the password.
To ensure a high level of security for user accounts in the Active Directory domain, an administrator must configure and implement a domain password policy. The password policy should provide sufficient complexity, password length, and the frequency of changing user and service account passwords. Thus, you can make it hard for an attacker to brute-force or capture user passwords when sending over a network.
What is the Active Directory Default Password Policy
By default, Active Directory is configured with a default domain password policy. This policy defines the password requirements for Active Directory user accounts such as password length, age, and so on.
This password policy is configured by group policy and linked to the root of the domain. You can view the default password policy using one of two ways.
- Using the GPMC
- Using PowerShell Scripts
Using the GPMC
- Go to Start Menu → Administrative Tools → Group Policy Management.
- In the console tree, expand the Forest and then Domains. Select the domain for which the Account policies have to be set.
- Double-click the domain to reveal the GPOs linked to the domain.
- Right-click Default Domain Policy and select Edit. A Group Policy Editor console will open.
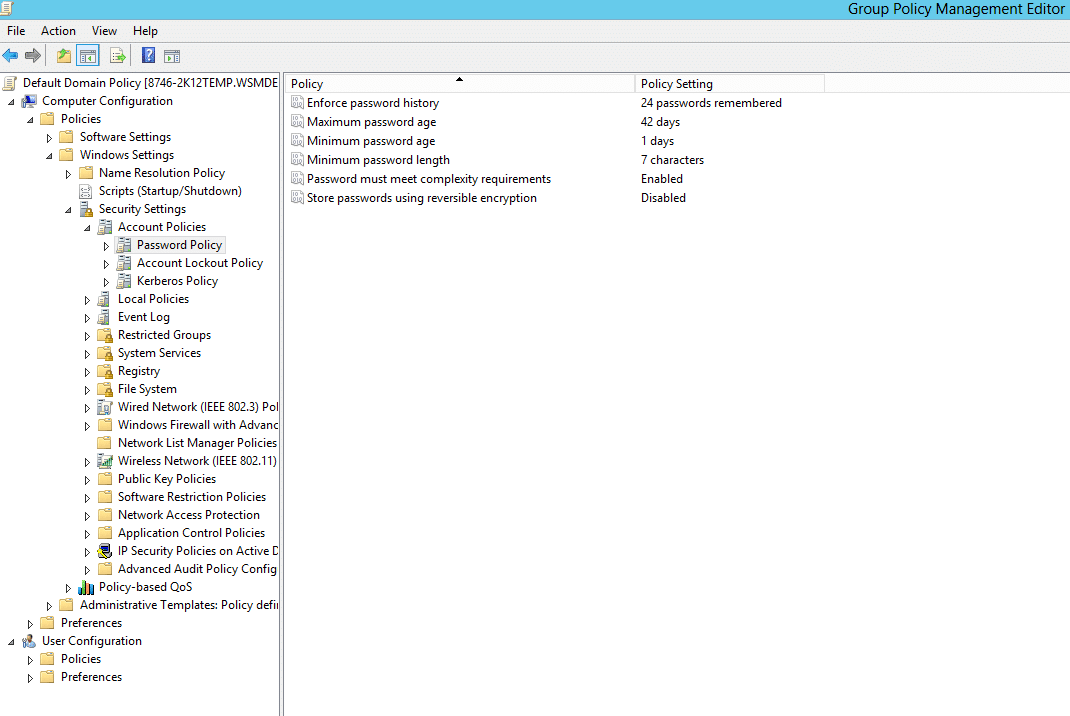
- Now, navigate to Computer Configuration → Policies → Windows Settings → Security Settings → Account Policies → Password Policy.
- Double-click Password Policy to reveal the six password settings available in AD. Right-click any one of these settings and select Properties to define the policy setting
- The Properties dialog box of each policy setting will have two tabs. The Security Policy Setting tab is where the value for that setting is set. The Explain tab gives a brief description of the policy setting and its default values.
- In the Security Policy Setting tab, check the Define this Policy Setting check box and enter the desired value. Click Apply and then OK.
Using PowerShell Script
You can also view the default password policy with Powershell using this command.
Get-ADDefaultDomainPasswordPolicy
Understanding Password Policy Settings
So far, we have seen how to view and change the policy. But you must know what each of these default settings means, so you can make the required changes. So, let’s take a look at each of the settings.
Enforce Password History
This setting determines the number of new passwords that have to be set before an old password can be reused. It ensures that old passwords are not used continuously by users which will render the Minimum Password Age policy setting useless. The value can be set between 0 and 24. The default value is 24 on domain controllers and 0 on stand-alone servers.
For example, if the Enforce Password History value is set to 10, then the user must set 10 different passwords when the password expires before setting his/her password to an old value.
If the value is set to 0, then the password history is not remembered, and the user can reuse their old password when their password expires.
Maximum Password Age
This setting determines the maximum number of days a password can be used. Once the maximum password age expires, users must change their password. It ensures that users don’t stick with one password forever. The value can be set between 0 and 999 days. The default value is 42.
For example, if the Maximum Password Age value is set to 60, then the user must change his/her password after every 60 days.
If the value is set to 0, then the password never expires, and the user is not required to change his/her password ever.
Minimum Password Age
This setting determines the minimum number of days a password must be in use before it can be changed. Only when the minimum password age expires, users are allowed to change their password. It ensures that users don’t change their passwords too often. The value can be set between 0 and 999 days. The default value is 1 for domain controllers and 0 for stand-alone servers.
For example, if the Minimum Password Age is set to 10, then the user cannot change his/her password for 10 days after the last password change.
This setting is used to ensure the effectiveness of Enforce Password History setting. If the Minimum Password Age is set to 0, then the user can change his/her password every 2 minutes or so until the value set for Enforce Password History is reached and reuse his/her favorite old password. By setting the Minimum Password Age to a certain value, a user cannot change his/her password often enough to render the Enforce Password History setting ineffective.
The value for Minimum Password Age should always be less than the Maximum Password Age.
Minimum Password Length
This setting determines the minimum number of characters a password should contain. The value can be set between 0 and 14. The default value is 7 on domain controllers and 0 on stand-alone servers.
For example, if the Minimum Password Length is set to 6, then the password must contain at least 6 characters.
If it is set to 0, then no password is required.
Passwords must meet complexity requirements
This setting determines whether the password must meet the complexity requirements specified. If this setting is enabled, passwords must meet the following requirements.
- Not contain the user’s account name or part of the user’s full name that exceed two consecutive characters
- The password is at least six characters long.
- The password contains characters from at least three of the following four categories:
- English uppercase characters (A – Z)
- English lowercase characters (a – z)
- Base 10 digits (0 – 9)
- Non-alphanumeric (For example: $, #, or %)
By default, this setting is enabled on domain controllers and disabled on stand-alone servers.
Store Passwords using reversible encryption
This security setting determines whether the password is stored using reversible encryption. If a password is stored using reversible encryption, then it becomes easier to decrypt the password. This setting is useful in certain cases, where an application or service requires the username and password of a user to perform certain functions. This setting should be enabled, only if it is necessary. By default, this setting is disabled.
Blocking Inheritance on Domain Controllers
If inheritance is blocked on the domain controllers (DCs), password policy settings from policies linked at the root domain will be ignored. This eventually means that the password policy settings changes in that GPO will be ignored and whatever the current password policy is will be applied on the domain. However, linking the GPO directly to the domain controllers has no effect. Administrators have to either remove the blocked inheritance on the domain controller’s OU or set the link at the root domain to ‘enforced’. As long as the policy appears in the Group Policy Inheritance list, the settings should take effect.
People also read
Fine-Grained Password Policy: A Step-by-Step Configuration Guide






