Active Directory (AD) Group Policy Objects (GPOs) are used to centrally manage user account settings, system configurations, and access to network resources. Here are some of the important benefits of using GPOs to configure shortcuts on user desktops:
- Deploy shortcuts to apps, links, file objects, and shell objects.
- Target specific user systems based on IP address range, MAC address range, operating system, and more.
Decide where the shortcut should appear on the user systems, and specify the exact location path.
Follow these steps to add shortcuts using Group Policy:
Launch the Group Policy Management Console (GPMC).
Open the Run dialog box >> Type gpedit.msc >>Click OK
Add the shortcut extensions to an already existing Group Policy or create a new Group Policy and add shortcuts.
- In the left navigation pane, go to Forest > Domains and click the intended domain name from the list.
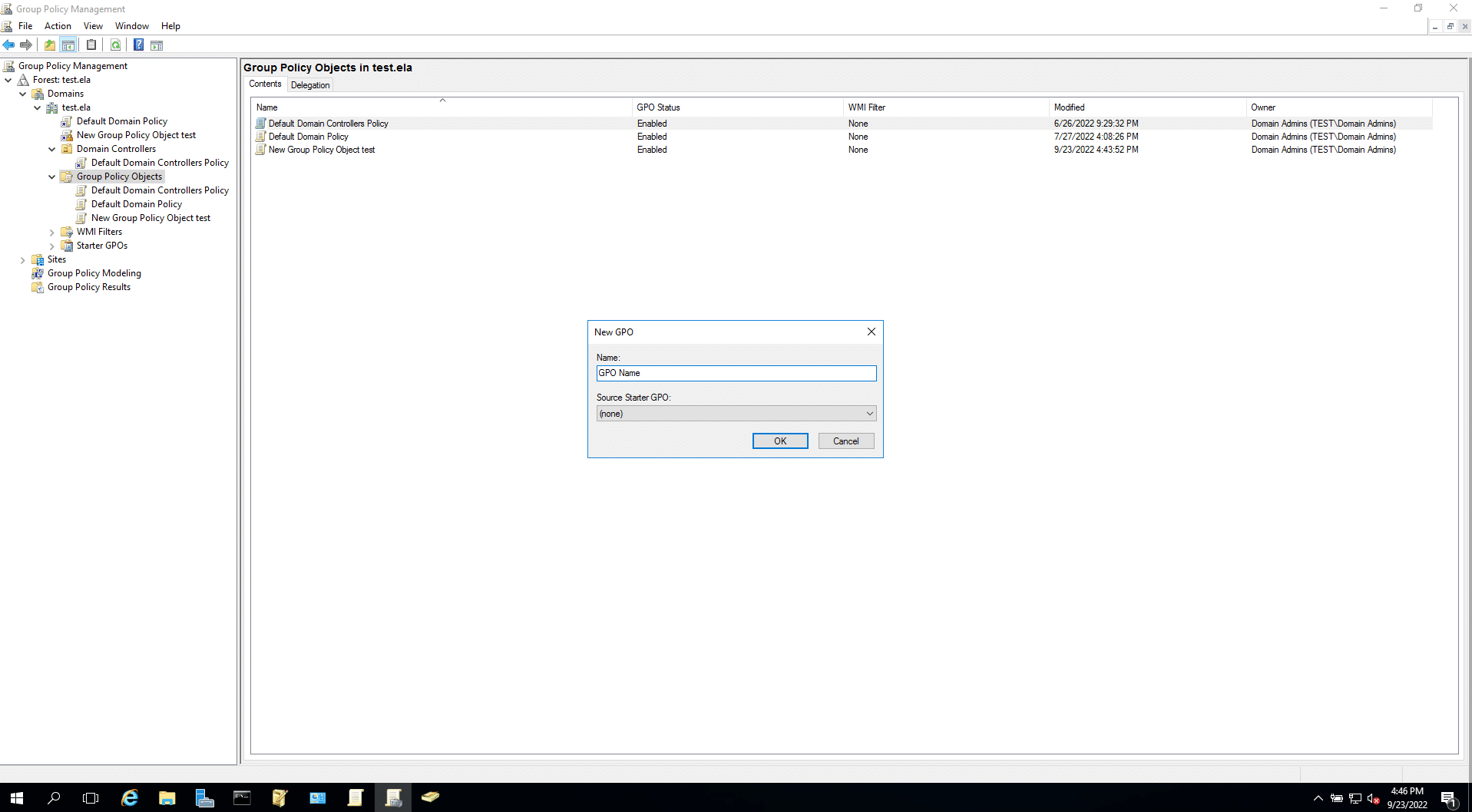
- Right-click Group Policy Objects > New and enter the GPO name. Select that GPO from the left pane, configure the settings, and link the GPO to the AD objects you want to target. This will complete the creation of a new GPO and add it to the AD hierarchy.
Adding shortcuts:
- Right-click the newly created Group Policy > Edit.
- Go to Computer Configuration or User Configuration > Preferences > Windows Settings > right-click Shortcuts > New > Shortcut.
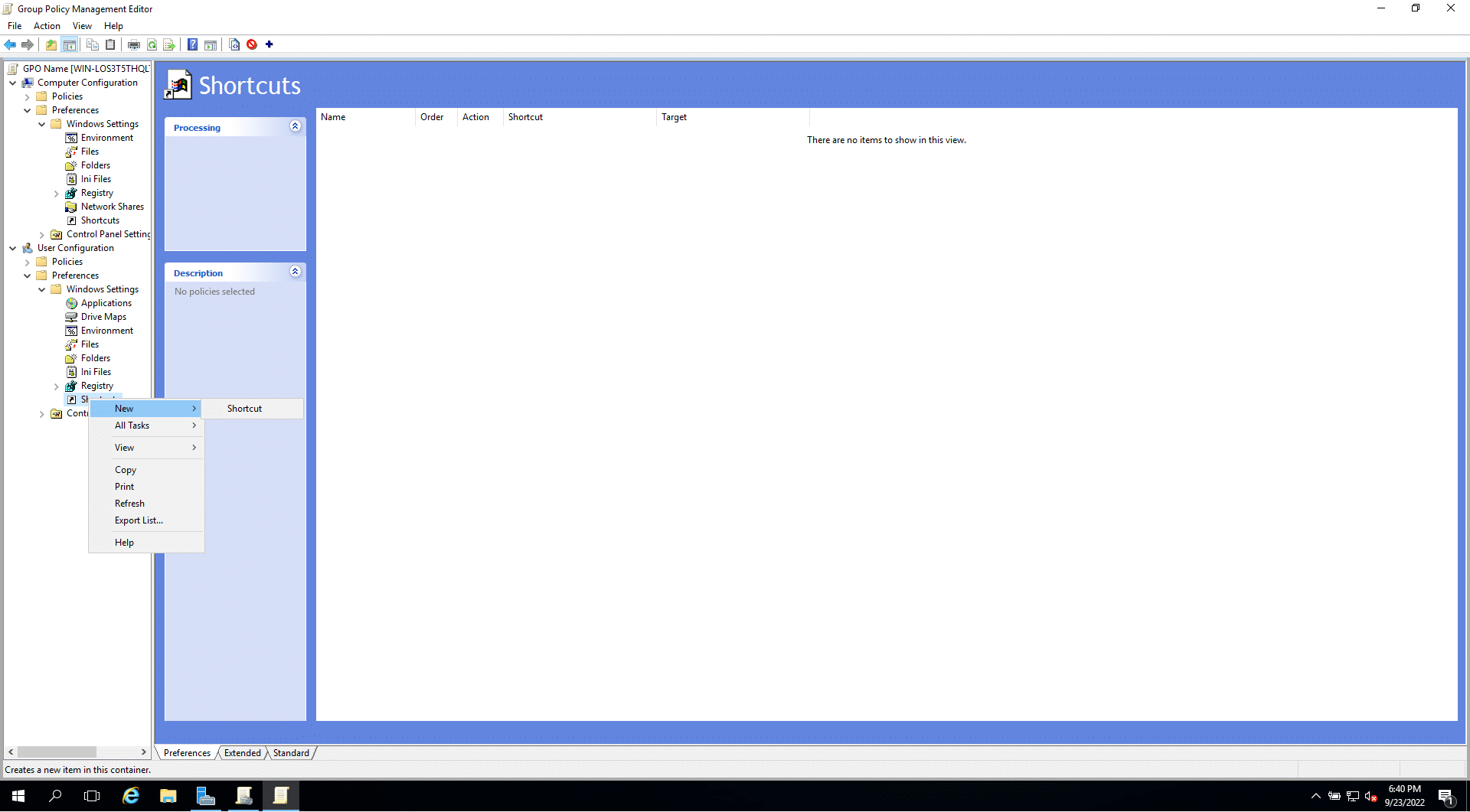
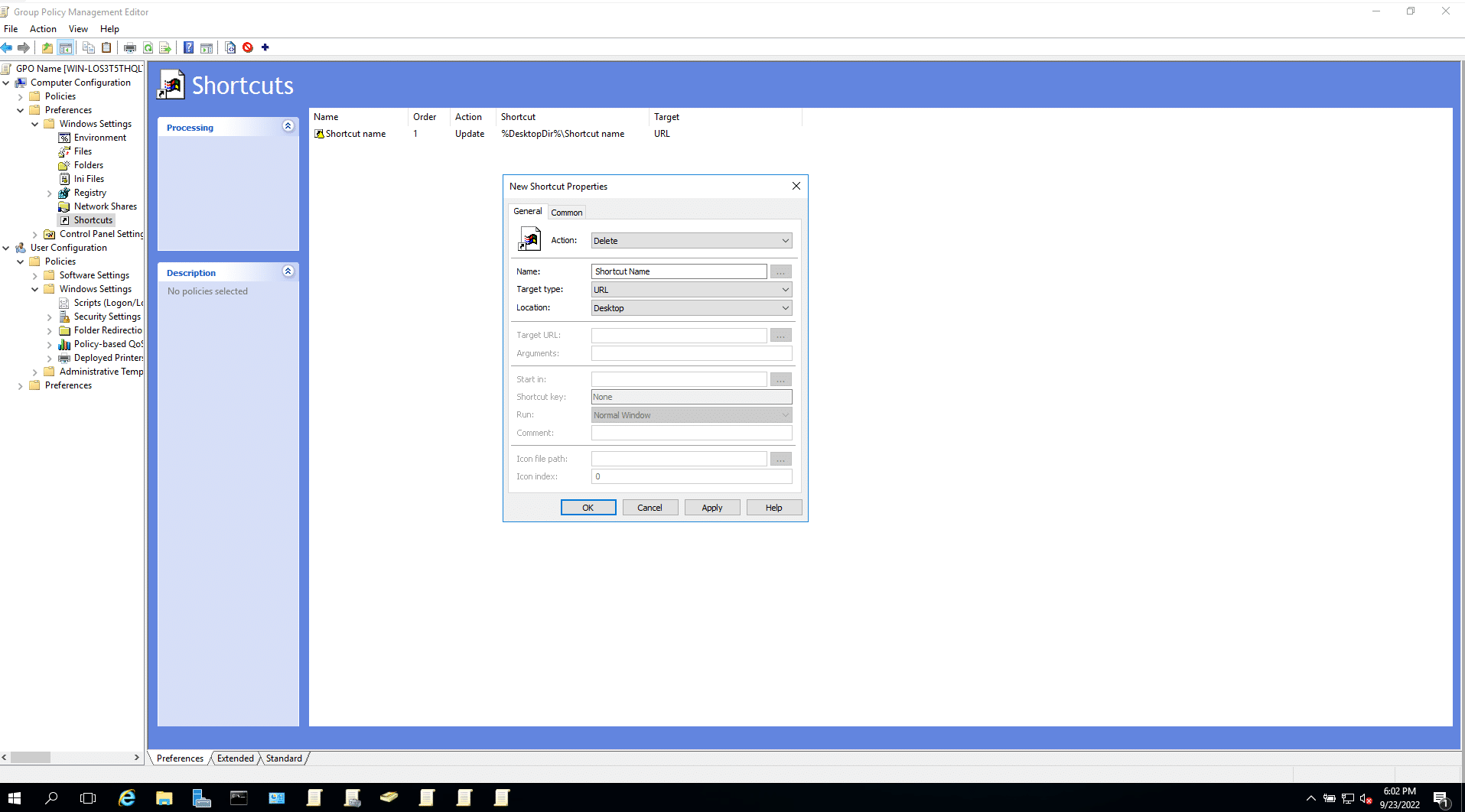
The shortcut settings window will open. The following are some of the important fields to be customized:
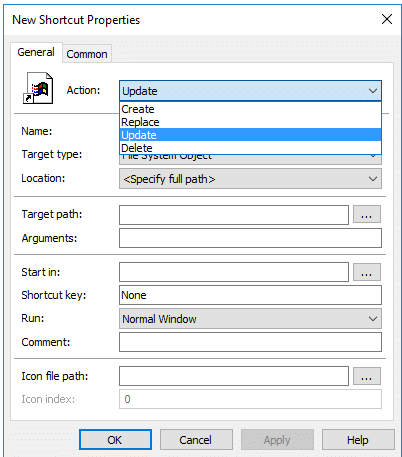
Actions: Create, Update, Replace, or Delete [View in detail]
- Create: A new GPO will be added.
- Update: The new changes will be applied to the already existing GPO settings. If the GPO doesn’t exist, it’ll be created.
- Replace: The entire GPO and the settings will be deleted and replaced.
- Delete: All the actions implemented through the GPO will be disabled and removed.
Target type: File System Object, URL, or Shell Object
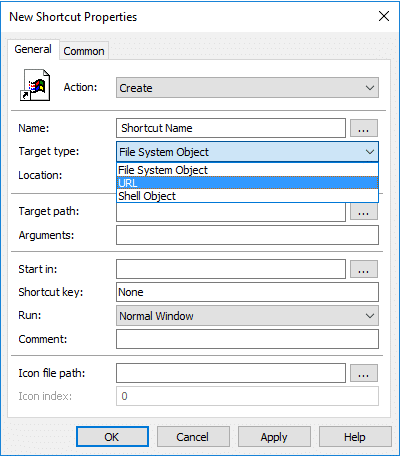
Location: Enter where the shortcut should appear in the targeted systems. <path>/<name of the shortcut>
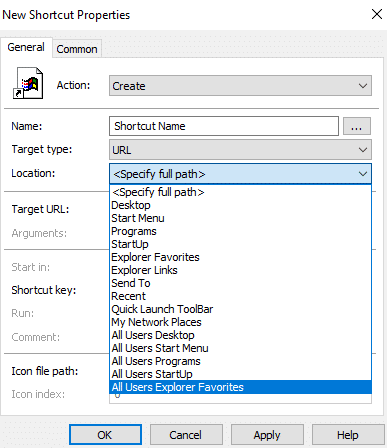
Target Path, URL, or Object: Enter where the shortcut will lead to when clicked.
- Target Path: This option is for file system objects. Enter the UNC path where the object is located in the local network.
- Target URL: This option is for target type: URL. Enter the website or FTP URL.
- Target Object: This option is for shell objects. Choose the targeted shell object from the list of options.
Shortcut Key: Enter the combination of keys to open the shortcut.
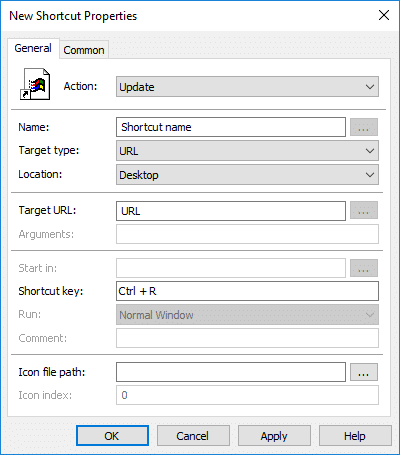
Icon file path: If you have an icon image associated with the shortcut, you can enter the path of the icon file here.
Once you have edited all the settings, open your Windows Command Prompt, run the gpupdate /force command, and reboot your system to implement the new Group Policy changes immediately.
User-level targeting
In the shortcut properties dialog box, you can see two tabs: General and Common. The General tab is used to add and modify shortcuts as mentioned in Step 3. The Common tab is used to configure user-level targeting.
Go to the shortcut properties > click the Common tab > check the Item-level targeting option > click Targeting… > New Item.
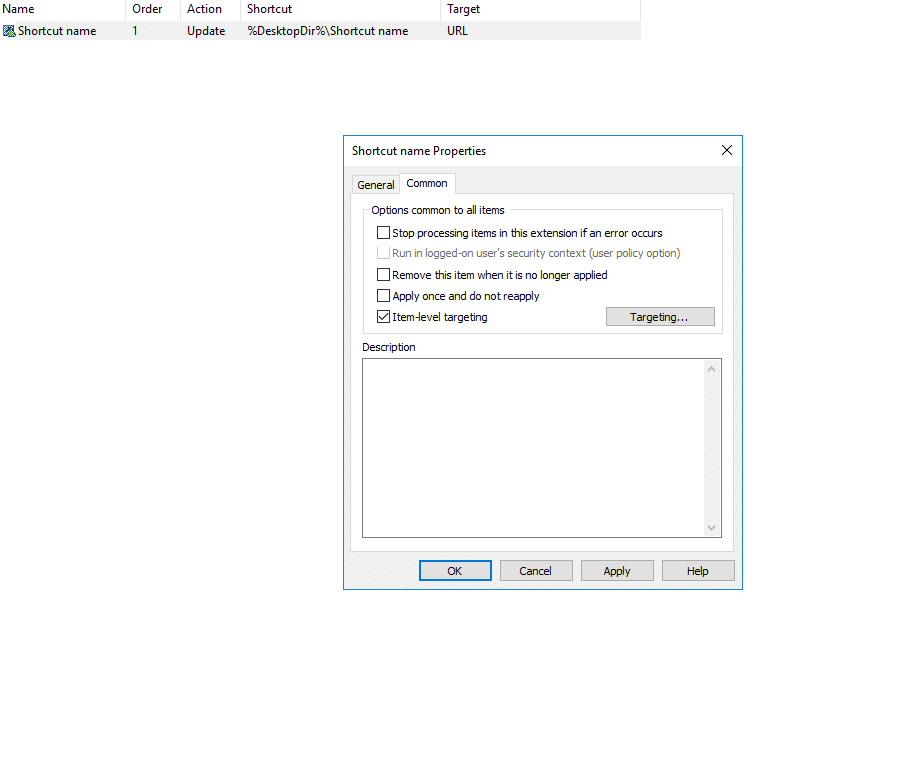
A list of options will be displayed to target specific systems based on IP address range, network connection, operating system, CPU speed, RAM, site, terminal session etc.
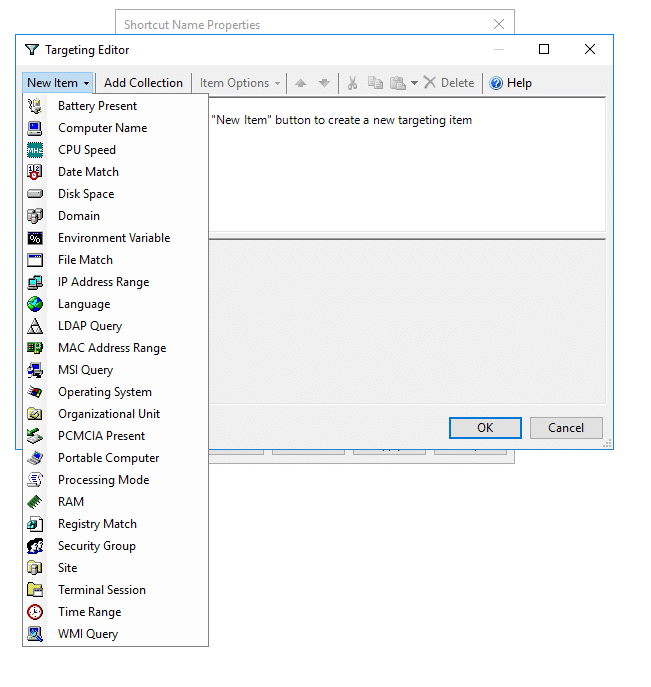
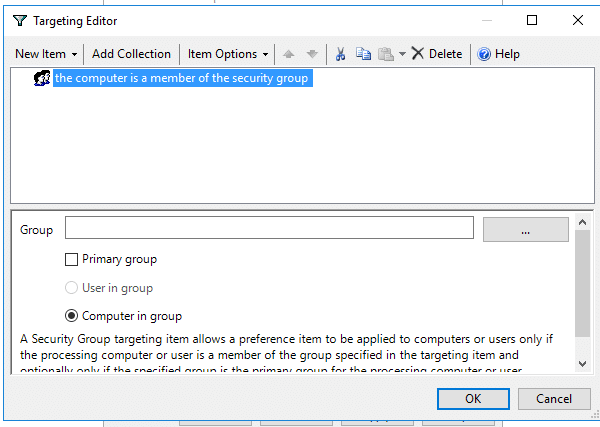
You can also define a security group and add that to the item-level targeting.
Removing shortcuts
Deleting the shortcuts on user systems or deleting the GPO on the domain controller using the GPMC will be ineffective. You need to change the GPO Actions to Delete and apply the settings to remove the shortcuts permanently from the user systems.