Administrators are well aware of the fact that users and groups occupy different levels of their organization’s hierarchy and do not all have the same privileges. Some accounts demand a stronger password policy than others for obvious security reasons.
Fine-grained password policy and PSO
Fine-grained password policy (FGPP) brings with it the capability of setting different password and account lockout policies for different sets of users in the same domain, thus making the AD environment more secure. FGPPs widen the scope of password security by having multiple password policies within a single domain.
Fine-grained password policies are deployed using password settings objects (PSOs). A PSO contains all the same password settings that exist in all other GPOs. To apply different settings to sets of users, administrators need to create a new PSO and configure the settings as per requirement. When a PSO is applied to a user, the user no longer uses the password policy deployed by Group Policy. Instead, they use the specified PSO settings.
To learn more about fine-grained password policies, click here.
Active Directory Administrative Center (ADAC)
The Active Directory Administrative Center is a Windows PowerShell based command-line interface through which administrators can easily perform data management and routine IT tasks from a single console having a visually appealing GUI. The ADAC gets installed automatically when the Active Directory Domain Services (AD DS) role is installed for Windows Server 2012 domain controllers and above. ADAC in Windows Server 2012, comes with enhanced fine-grained password policy features, allowing administrators to create and manage PSOs.
Opening the ADAC
The following are some ways to open the ADAC:
Method 1:
- Click the Start button and type Active Directory Administrative Center.
- Hit Enter.
Method 2:
- Click the Start button and type Server Manager.
- Hit Enter.
- Click on Tools. From the drop-down menu, select Active Directory Administrative Center.
Method 3:
- Click the Start button and type dsac.exe.
- Hit Enter.
Creating a PSO
To create a PSO:
- In the ADAC, go to System → Password Settings Container.
- Right click and select New followed by Password Settings.
- In the Create Password Settings window that appears, fill in the details required, including name, precedence, password age options, and more.
- Click Add to select the group on which you want the policy to take effect.
- Click OK and Close.
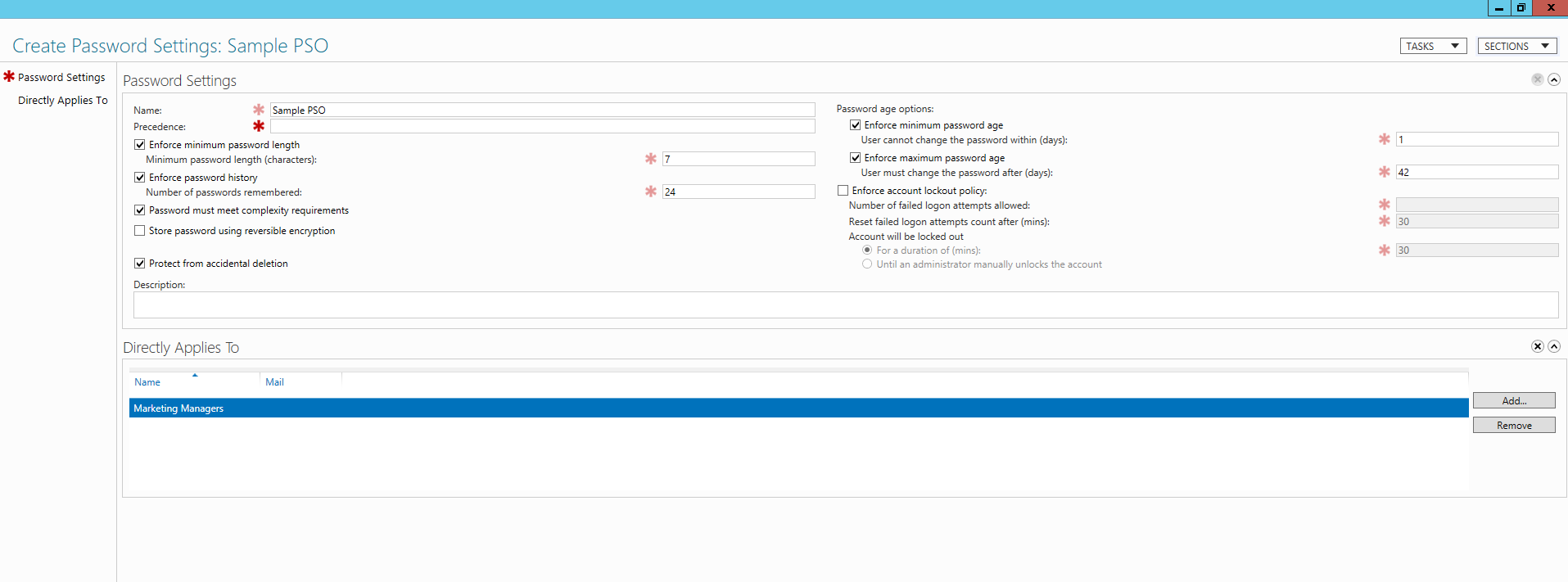
Every PSO comes with an attribute known as ‘precedence’ which helps resolve conflicts that arise out of multiple PSOs are applied on a user object. It is an integer valued attribute and value of ‘1’ indicates the highest precedence. Note that merging of settings from multiple PSOs is not possible.
Viewing resultant settings in a PSO
To view the resultant policy settings on a user:
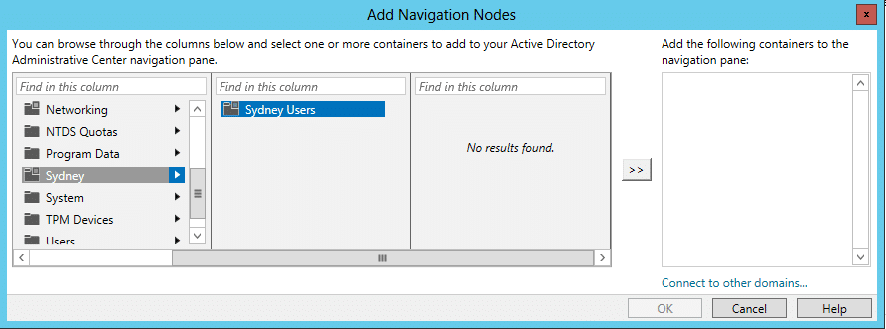
- In the ADAC, go to Manage → Add Navigation Nodes.
- Select the required domain and user, and click OK.
- In the Tasks pane, click View Resultant Password Settings.
Editing a PSO
To edit a PSO:
- In the ADAC, go to System → Password Settings Container.
- Select the PSO you want to edit. Right click and select Properties.
- Modify the values as required.
- Click OK.
Deleting a PSO
To delete a PSO:
- In the ADAC, go to System → Password Settings Container.
- Select the PSO you want to delete. Click Delete.
- Click OK.
Fine-grained Password Policy Best Practices
When implementing FGPPs, there are several things to think about before creating and applying FGPPs.
- Each PSO must have a precedence index number. PSOs with a higher precedence index, like 1, take priority over those with a lower precedence index, like 10.
- PSOs can be applied to users and groups. When possible, apply PSOs to groups.
- Understand PSO precedence. While PSOs can be applied to multiple users and groups, only one PSO ever applies to a user account. The PSO with the highest precedence index, i.e. closest to 1, will apply. The msDS-ResultantPSO attribute in AD exposes the resultant PSO for a user object if you want to check it. PSOs linked to user accounts always take precedence over those linked to groups.
- Make sure that all PSOs have a unique precedence index number. If two PSOs have the same precedence index number, the PSO with the lowest GUID is applied.
- If you want to apply a PSO to all the users in an Organizational Unit (OU), you will need to create a group that contains all the members of the OU and apply the PSO to the group. If the users in the OU change, you must update the group membership.
- Use password and account lockout policy settings in the Default Domain Policy GPO for most users and create PSOs for smaller specific groups of users.
- Give PSOs meaningful names.
People also read
Active Directory Password Policy
Fine-Grained Password Policy: A Step-by-Step Configuration Guide







