1. Introduction
Hey curious IT wizards! Let us take a broad and in-depth look into what is Azure Multi Factor Authentication (MFA), how it works, why it is important and all the steps involved in creating, configuring, managing and troubleshooting. Now, before delving deep into the nuances of Azure Multi Factor Authentication, if you are a well-aware of the underlying knowledge, you can directly skip to the Step – 3. Prerequisites for Setting Up Azure MFA.
1.1 What is Azure MFA?
Security lapses and unwanted access to private data have grown to be major worries in today’s digital world. Organizations are using Multi-Factor Authentication (MFA) systems to fend off these threats. Microsoft created Azure MFA, a strong authentication technique that strengthens user accounts’ security and aids in preventing illegal access.
It is a cloud based service which verifies user identities by requesting additional identification documentation from them as part of the authentication process. This extra evidence usually manifests as a second factor, like a call, text message, or mobile app notification. By this way, organizations using Azure can significantly lower the risk of unauthorized access and safeguard their priceless resources by implementing the multi factor authentication.
1.2 Why implementing Azure MFA is important?
Due to the growing sophistication of cyber threats, implementing Azure MFA is essential in today’s digital environment. Passwords and other conventional authentication methods are no longer sufficient on their own. Passwords are easily compromised by hackers using various techniques like phishing attacks and brute-force attacks.
By requiring users to provide a second factor of authentication, it adds an extra layer of security, making it much more challenging for attackers to gain unauthorized access. Hackers would still require the second factor, which is typically something the user owns, like a mobile device, even if they were able to guess the user’s password.
These are the main reasons why organizations should improve the security of their systems and safeguard sensitive data, such as customer information, intellectual property, and financial records, by implementing the MFA. Additionally, it aids businesses in adhering to industry standards and compliance guidelines that demand more robust authentication procedures.
Furthermore, it gives users within an organization the freedom to select from a variety of authentication techniques, making it user-friendly. Users are given the option to choose the method that best suits their preferences and convenience from options like phone calls, text messages, or mobile app notifications.
Overall, implementing Azure MFA is an essential step towards bolstering security, mitigating risks, and safeguarding critical assets in the face of ever-evolving cyber threats.
2. Understanding Azure MFA
Now let us take a step back and look into underlying factors of what is MFA, what are the benefits of Azure MFA and how it works.
2.1 What is Multi-Factor Authentication?
By requiring multiple forms of authentication, Multi-Factor Authentication (MFA) adds an additional layer of security to user accounts. In the case of Azure MFA, it adds an additional step to the login process to ensure that unauthorised access is prevented even if a user’s password is compromised.
It uses a combination of factors for authentication, such as something the user is, something they have, or something they know (such as a password or trusted device) (biometric data like fingerprint or face recognition). What makes it noteworthy is that, it greatly improves user account security by requiring multiple factors.
2.2 Benefits of Azure MFA
Implementing Azure MFA provides several key benefits:
- Increased Security: It adds an additional layer of verification beyond just a password, reducing the risk of unauthorised access. This protects resources and sensitive data.
- Compliance Requirements: Regarding the protection of sensitive data, many industries have specific compliance requirements. it offers an additional layer of security that aids in fulfilling these requirements.
- Convenience for the user: It supports a number of authentication techniques, such as notifications from mobile apps, phone calls, text messages, and hardware tokens. Users are free to select the method that best suits their needs without sacrificing security.
- Seamless integration: It integrates without difficulty with a number of Microsoft services and products, including Azure Active Directory (AD), Office 365, and other cloud-based services.
2.3 How Azure MFA Works
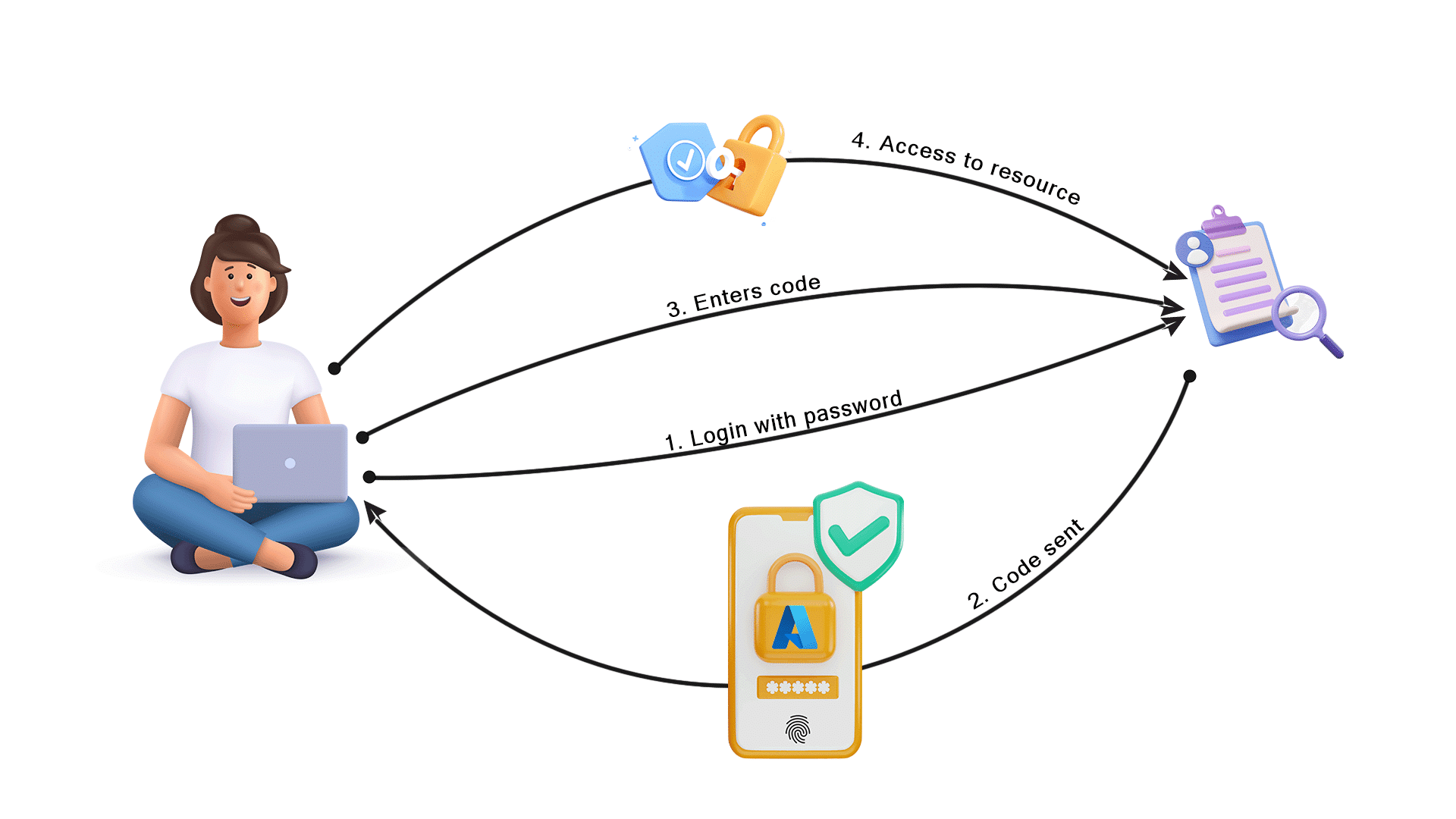
As we saw, Azure MFA verifies a user’s identity by combining multiple authentication factors. The following steps makeup the typical flow of Azure MFA:
Step 1 – User initiates login:
The user attempts to log in to an Azure AD-protected resource, such as a web application or VPN.
Step 2 – Username and password:
As the first factor of authentication, the user provides their username and password. This is how authentication has traditionally been done.
Step 3 – Additional verification:
Following a successful username and password entry, Azure MFA prompts the user to provide additional verification.
Step 4 – Selecting an authentication method:
The user selects their preferred method of authentication, such as receiving a notification on their mobile app, receiving a phone call, or entering a verification code.
Step 5 – Second factor authentication:
Using the selected method, the user completes the second factor authentication. This may entail accepting the notification through their mobile app, picking up the phone, or entering the received verification code.
Step 6 – Access is granted:
The user is given access to the protected resource if both the username/password and second factor authentication are successfully verified.
By combining these authentication factors, you can increase security and make sure that only authorized users have access to resources and sensitive data.
3. Prerequisites for Setting Up Azure MFA
There are a few prerequisites you must make sure are in place before you can set up Azure Multi-Factor Authentication (MFA) for your organization. You will be led through the necessary requirements and preparations in this section.
3.1 Azure subscription requirements
You must have an active Azure subscription in order to use Azure MFA. If you don’t already have one, you can purchase a subscription or sign up for a free trial through the Azure portal (https://portal.azure.com).
Note: Verify that you have the right rights to manage Azure resources inside of your subscription.
3.2 Supported authentication methods
Different authentication techniques supported by Azure MFA can be used to confirm users’ identities. Some of the most frequently used techniques include:
- Phone call verification: Users will receive an automated phone call to verify their identity.
- SMS verification: Users will receive a verification code via SMS on their registered mobile number.
- Mobile app verification: Users can opt to use a mobile app, such as the Microsoft Authenticator app, to receive push notifications for verification.
- OATH hardware tokens: Physical hardware tokens, like YubiKey, can be used for authentication.
- Email verification: Users will receive a verification code via email.
Note: Before implementing Azure MFA, decide which authentication techniques are appropriate for your business and confirm that your users have the devices or accounts required for those techniques.
3.3 Preparing your environment
Before enabling Azure MFA, there are a few environment configurations you need to review and prepare:
Azure Active Directory (AD):
Make sure your Azure subscription is linked to an Azure AD tenant. You can create one from the Azure portal if you don’t already have one.
User accounts:
Verify that each user who will be enrolled in Azure MFA has a functioning Azure AD user account. Create user accounts or use Azure AD Connect to synchronize your on-premises Active Directory with Azure AD as necessary.
Conditional Access policies:
If you have any current Conditional Access policies, review them to see if they comply with your MFA requirements. In order to impose multi-factor authentication for particular scenarios or applications, Azure MFA can be integrated with Conditional Access policies.
Application compatibility:
Make sure your on-premises applications are compatible with Azure MFA if they need user authentication. For seamless MFA support, some applications might need additional configuration or integration.
Reviewing and assembling these requirements will get you ready to start setting up Azure MFA for your company. The implementation process will go more quickly and securely if your environment is organized and well-prepared.
4. Steps to implement Azure MFA
4.1 Creating an Azure Active Directory (AD) tenant
To set up Azure Multi-Factor Authentication (MFA), the first step is to create an Azure Active Directory (AD) tenant. Follow these steps:
- Sign-in with your Azure account from the Azure portal (https://portal.azure.com).
- From the left menu, click “Azure Active Directory“.
- In the Azure Active Directory pane, select “Create a tenant“.
- Fill in the required information, such as the organization name, initial domain name, and country or region.
- To validate the information click on “Review + Create“.
- Now, to create the Azure AD tenant, click on “Create“.
Once the Azure AD tenant is created, you can proceed to configure Azure MFA.
If you want to know more about creating Azure AD tenant, visit this article: A comprehensive guide on how to set-up an Azure AD tenant
4.2 Configuring Azure MFA settings
4.2.1 Enabling Azure MFA for users
To enable Azure MFA for users, follow these steps:
- From Azure portal, navigate to the Azure AD tenant you created above.
- From the left menu, click “Azure Active Directory“.
- Under the “Security” tab, select “Authentication methods“.
- Now from the Authentication methods pane, click on “MFA settings“.
- In the MFA settings pane, click on “Users“.
- Now, from the Users pane, select all the users for whom you want to enable Azure MFA.
- Select “Enable” to enable Azure MFA for the selected users.
If you want to understand more about configuring Azure AD tenant, visit this article: A step-by-step guide on how to Configure Azure AD Tenant
4.2.2 Selecting authentication methods
To select authentication methods, follow these steps:
- From the MFA settings pane, click on “Methods“.
- In the Methods section, you will see a list of available authentication methods.
- Select the desired authentication methods that your users need to use for multi-factor authentication. The following forms of authentication are provided by Microsoft, additionally.
- Microsoft Authenticator
- Authenticator Lite (in Outlook)
- Windows Hello for Business
- FIDO2 security key
- OATH hardware token (preview)
- OATH software token
- SMS
- Voice call
- Now, save the selected authentication methods.
4.2.3 Customizing MFA settings
To customize Azure MFA settings, follow these steps:
- From the MFA settings, click “Customize“.
- In the Customize pane, you can configure various settings such as options like MFA verification, bypass, and fraud alerts.
- Adjust the settings according to your organization’s requirements.
- And save the customized MFA settings.
4.3 Implementing Azure MFA for Azure AD users
To implement Azure MFA for Azure AD users, follow these steps:
- From the Azure portal, navigate to the Azure AD tenant you created.
- Click on “Azure Active Directory” from the Navigation section.
- Under the “Security” section, open “MFA service settings“.
- In the MFA service settings, click “Azure AD user settings“.
- From the User settings, you can configure various options such as MFA enforcement, trusted IPs, and app passwords.
- Adjust the settings according to your requirements.
- Then, save the Azure AD user settings.
4.4 Enabling Azure MFA for on-premises applications
To enable Azure MFA for on-premises applications, follow these steps:
- Navigate to your Azure AD tenant.
- From the left navigation menu, click on “Azure Active Directory“.
- Under the “Security” section, click “MFA service settings“.
- In the MFA service settings pane, click on “App registrations.”
- To register your on-premises application, click on “New registration”, in the App registrations section.
- Fill-in the required information, such as the application name and redirect URI.
- After completing the registration, select the registered application.
- Click on “Manage“, to perform MFA configuration for the on-premises application.
- Follow the instructions provided to set-up Azure MFA for the on-premises application.
5. Best Practices for Azure MFA Setup
5.1 User Enrollment and Communication
Implementing Azure Multi-Factor Authentication (MFA) involves enrolling users and communicating the enrollment process effectively. Here are some best practices to follow:
5.1.1 Educate Users on the Benefits:
Give a concise explanation of the value of Azure MFA and how it improves account security. Draw attention to the extra layer of security it offers and the function it plays in preventing unauthorised access.
5.1.2 Provide Clear Instructions:
Make user-friendly instructions or guides that describe the steps involved in signing up for Azure MFA. To make it simpler for users to understand and follow along, add screenshots and illustrations.
5.1.3 Send Email Notifications:
Users should receive email notifications alerting them to the impending implementation of Azure MFA. Include any necessary information, such as instructions and enrollment deadlines. For clarity, use clear, concise language.
5.1.4 Conduct Training Sessions:
Consider holding webinars or training sessions to explain the enrollment process and address any queries users might have. Assist users directly if necessary to ensure a smooth enrollment process.
5.2 Monitoring and Reporting
Effective management of Azure MFA requires both monitoring and reporting. The following recommendations will help you create a strong monitoring and reporting system:
5.2.1 Enable Azure AD Sign-In Logs:
To track and keep track of user sign-ins, including MFA events, enable the Azure AD Sign-In logs. This gives insight into MFA usage and makes it easier to spot any suspicious behaviour or potential security flaws.
5.2.2 Implement Azure AD Identity Protection:
Advanced security features like risk-based conditional access policies and fraud detection are offered by Azure AD Identity Protection. Set up policies so that risky sign-in attempts are blocked or subject to additional authentication.
5.2.3 Review MFA Usage Reports:
Review MFA usage reports frequently to learn more about user adoption rates and the success of your MFA implementation. Determine any patterns, trends, or areas that might need more study or improvement.
5.2.4 Set Up Alerts:
Set up alerts for important occurrences like repeated MFA attempts that fail, erratic sign-in behaviour, or modifications to the MFA settings. For centralised monitoring, alerts can be integrated with Azure Monitor or sent via email.
5.3 Security Considerations
To ensure the highest level of protection, security best practises must be taken into account when configuring Azure MFA. Here are a few suggestions:
5.3.1 Enforce Strong Authentication Methods:
Encourage users to use secure authentication techniques like the Microsoft Authenticator app or hardware tokens. Encourage against using SMS-based authentication due to attacks involving SIM swapping.
5.3.2 Implement Conditional Access Policies:
Azure AD Conditional Access policies that are based on user roles, device trust, location, and risk level can be used to enforce MFA requirements. Using specific contextual factors, this adds an extra layer of security.
5.3.3 Regularly Update MFA Configurations:
Keep up with the most recent security updates, Azure MFA features, and best practises. Review and update your MFA settings frequently to stay current with changing industry standards and the threat landscape.
5.3.4 Conduct Security Awareness Training:
Users should be made aware of common security risks like phishing and social engineering strategies. Stress the value of keeping their MFA credentials safe and adhering to strict security procedures.
5.4 Troubleshooting Common Issues
Users may run into a few common problems while configuring and using Azure MFA. Following are some troubleshooting hints:
5.4.1 Provide Self-Service Password Reset:
Enable self-service password reset for Azure Active Directory so that users can quickly change their passwords if they lose them. As a result, the help desk has less work to do and users can quickly regain access.
5.4.2 Verify MFA Authentication Methods:
Make sure the chosen MFA authentication techniques are supported and correctly configured. To ensure seamless authentication, resolve any problems with phone numbers, email addresses, or token configurations.
5.4.3 Check for Compatibility Issues:
Check to see if Azure MFA and other programmes or systems in your environment have any compatibility problems. To resolve any conflicts, update pertinent software, drivers, or configurations.
5.4.4 Monitor Azure MFA Service Health:
By keeping an eye on the Azure Service Health dashboard, you can keep track of how the Azure MFA service is doing. Look for any incidents or outages that may be continuing and affecting MFA functionality.
Conclusion
In this article, we have explored the process of setting up Azure Multi-Factor Authentication (MFA). Keep in mind, that protecting the digital assets of your company is a shared responsibility. Azure MFA implementation strengthens your overall security infrastructure while also protecting your users. Take advantage of Azure MFA’s strength and incorporate it into your cybersecurity plan.
Stay proactive, stay secure!







