Microsoft has two solutions for deploying the requirements for Active Directory domain users’ passwords. The requirements, referred to as the password policy, can be deployed through Group Policy Objects (GPOs) or through Active Directory objects called fine-grained password policies (FGPPs). Both solutions have the same list of constraints, such as minimum password length and maximum password age, but the details around the implementation are radically different.
Deploying a password policy using a GPO is the seasoned solution since it was introduced when Active Directory was released in 2000.
In Active Directory, before the release of Windows Server 2008, you could only have one Password Policy and Account-Lockout Policy per domain. However, there are times when you need a group of users to have a different password policy. This is because it is best practice to enforce strong password policies to privileged accounts in the domain. For example, employees in the finance department may need a stronger password policy and account lockout policy than employees in the production department. Similarly, the manager of a department may need a different account policy than their subordinates.
Active Directory Fine-Grained Password Policy: An Introduction
With the release of the Windows Server 2008 Operating System, Active Directory gained one major feature that was missing in the previous versions. Fine-Grained Password Policy (FGPP), which gives AD the ability to set different password policies and account lockout policies for a different set of users in a domain was introduced.
The one drawback of using GPOs to apply a password policy on users is that the only password policy settings that will be applied to domain users will be in GPOs linked to the domain, containing password policy settings, and with the highest priority. Therefore, there can be only one password policy for all of the domain users in a single domain.
Fine-Grained Password Policies (FGPPs), on the other hand, are defined inside of Active Directory by creating a Password Settings Container. FGPP can be created using the Active Directory Services Interface Editor (ADSI Edit).
Creating a Fine-Grained Password Policy (FGPP)
The following steps describe how to create an FGPP:
- Open ADSI Edit tool, Start Menu → Administrative Tools → ADSI Edit
- In the Menu Bar on the ADSI Edit console, select Action → Connect to
- In the Connection Settings dialog box, select Default Naming Context as the connection point and Default Domain as the computer and click OK
- Now, double-click the Default Naming Context and then double-click DC=domainame,DC=com
- Double-click CN=System → CN=Password Settings Container
- Right-click CN=Password Settings Container and select New → Object
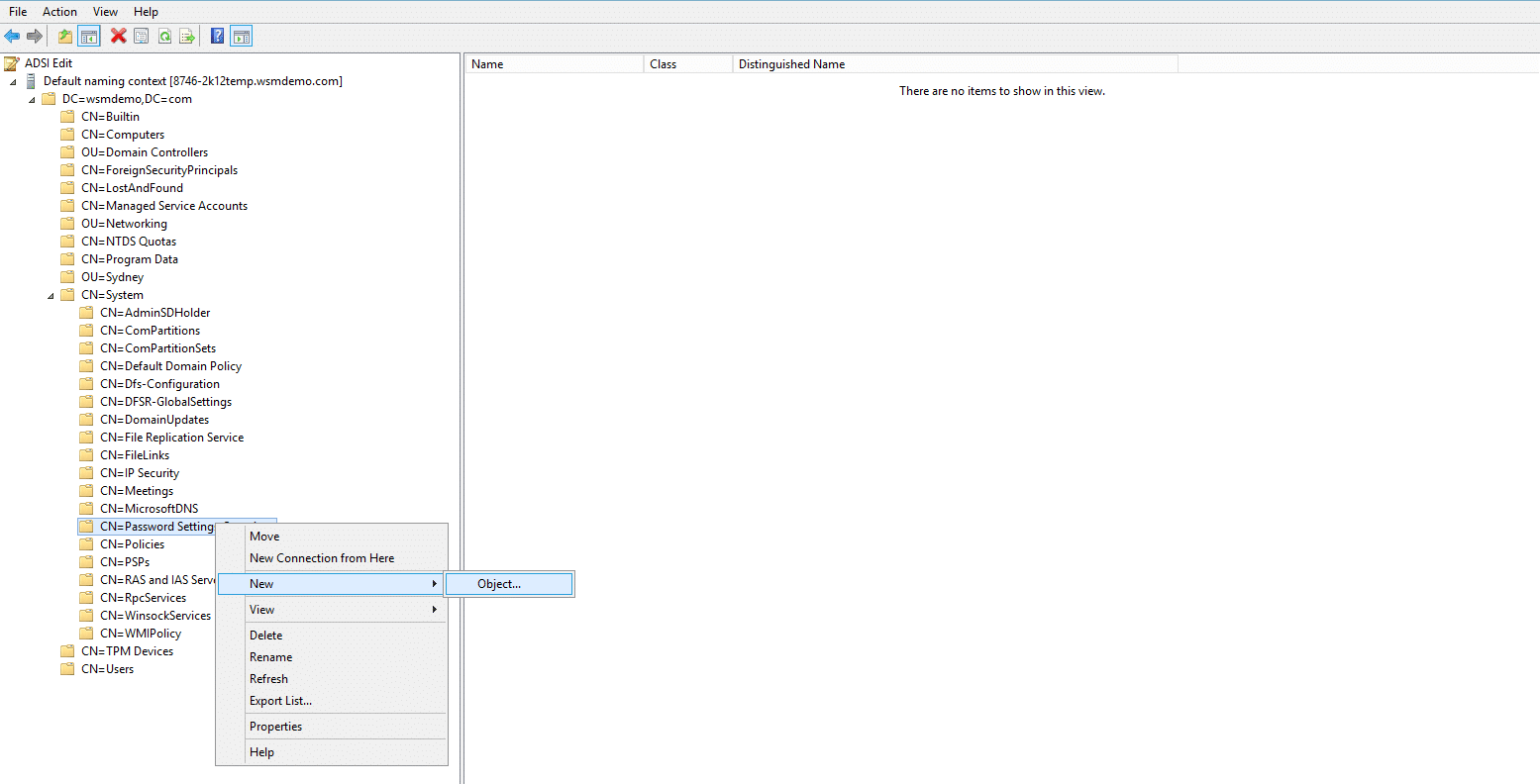
- In the Create Object dialog box, under select a class, choose msDS-PasswordSettings and click Next
- Enter the following values for all the attributes in the correct syntax and continue with the wizard.
msDS-LockoutDuration: 0:00:05:00
msDS-LockoutObservationWindow: 0:00:01:00
msDS-LockoutThreshold: 50
msDS-MaximumPasswordAge: 90:00:00:00
msDS-MinimumPasswordAge: (none)
msDS-MinimumPasswordLength: 12
msDS-PasswordComplexityEnabled: FALSE
msDS-PasswordHistoryLength: 24
msDS-PasswordReversibleEncryptionEnabled: FALSE
msDS-PasswordSettingsPrecedence: 3
- After entering appropriate values for each attribute, the Create Object wizard will show the Finish page
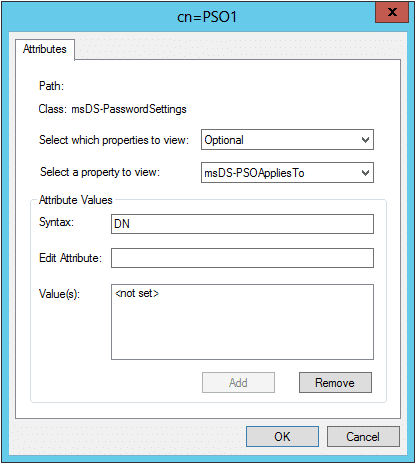
- In the Finish page, click More Attributes. Choose Both from the Select which properties to view drop down list and choose msDS-PSOAppliesTo from the Select a property to view drop down list
- Under the Attribute Values section, enter the distinguishedName of the user or group to which the FGPP will be applied and click Add. Multiple values can be added.
- Once all the users and groups are added, click OK and then click Finish to close the wizard
FGPP can be applied only to user objects and global security groups. FGPP cannot be applied directly to an OU. However, by creating a shadow group, FGPP can be applied to all users and groups in an OU. A shadow group is a global security group that is logically mapped to an OU to enforce the FGPP. By adding all the users in the OU as members of the shadow group, the FGPP applied to the shadow group will be enforced on the users as well. Use the below command to create and map a shadow group to an OU:
dsquery user “OU=TestOU,DC=domain1,DC=com” | dsmod group “CN=shadowgroup,OU=TestOU,DC=domain1,DC=com” –chmbr
When new users are added to the OU, run the above command to automatically add the new users as members of the shadow group and apply FGPP. By default, only members of the Domain Admins group can create and set FGPP to a user or group.
Fine-Grained Password Policy Precedence
The FGPP applied directly to a user takes precedence over the FGPP applied to the group in which the user is a member. Also, if more than one FGPP is applied to a user, then the FGPP with the lowest msDS-PasswordSettingsPrecedence will be applied. If two FGPPs with the same msDS-PasswordSettingsPrecedence are applied to a user, then the FGPP with the smallest GUID (Globally Unique Identifier) will be applied to the user.
To determine which FGPP is applied to a user, an attribute called msDS-ResultantPSO can be used. It holds the distinguishedName of the FGPP applied to the user. The msDS-ResultantPSO can be viewed through the Attribute Editor tab of the user properties in ADUC.
People also read
Managing GPOs in Active Directory


