What you will learn from this article:
Active Directory (AD) relies on the AD replication process to keep the information updated across all its domain controllers (DC) in the network. This replication is done through the multi-master replication method, where if the information is modified in one DC, that DC initiates the replication process to update the other DCs. You can learn more about AD replication in this article. However, in this replication method, if multiple DCs updates the same information, the update that stays is the one that was implemented last. This could not always be favourable. So, Microsoft introduced the single master replication method where one domain takes control over the entire replication process. However, this method posed yet another problem. Should the single master DC fail for some reason, the whole replication process would come to a standstill. To avoid this situation, Microsoft introduced Flexible Single Master Operations (FSMO) roles. In this article, we will take a look at what are AD FSMO roles, and what are the various types of FSMO roles.
Table of content
- What is FSMO?
- Types of FSMO roles
- Forest-wide operations master roles
- Identifying DCs with authorized FSMO roles
- Determining the Schema FSMO Holder in a Forest
- Determining the Domain Naming FSMO Holder in a Forest
What are Active Directory FSMO roles?
FSMO roles are replication roles, assigned to DCs by administrators. Each role takes care of a certain part of the replication process so that one DC does not have to monitor and control all the replication processes. Moreover, these roles are called ‘flexible’ because should a DC which has a role go down, its role can be taken up by another DC. Thus, FSMO roles are distributed to a group of DCs that communicate with themselves to ensure that replication continues seamlessly within the AD network. The DCs that have these roles are called the operations master, and since 2005, the operations master term has been in use over FSMO.
Types of Active Directory FSMO roles
There are a total of five FSMO roles in AD, which are as follows:
- Schema master
- Domain naming master
- RID master
- PDC emulator
- Infrastructure master
Certain operations master roles must be present at least once in every domain, and certain roles must be present at least once in a forest. Let’s take a look at the roles in detail.
Forest-wide operations master roles
These roles are ones that must appear at least once in a forest. They are as follows:
- Schema master
- Domain naming master
Note: There can only be one schema master and one domain naming master in a forest
Schema master
Any update or modification done to the schema must go via the schema master domain controller. To make such updates/modifications to the schema of a forest, access has been established with the schema master. There can be only one schema master in the entire forest.
Domain naming master
The domain controller holding the domain naming master role exclusively controls the addition or removal of domains in the forest.
There can be only one domain naming master in the entire forest.
- Any domain controller running Windows Server 2003 can hold the role of the domain-naming master.
- A domain controller running Windows 2000 Server that holds the role of domain naming master must also be enabled as a global catalog server.
Domain-wide operations master roles
These roles are ones that must appear at least once in a domain. They are as follows:
- Relative ID (RID) master
- Primary domain controller (PDC) emulator
- Infrastructure master
Note: Each domain in a forest can have only one RID master, PDC emulator, and infrastructure master.
RID master
It is the task of the RID master to allot sequences of relative IDs to each of the (numerous) domain controllers in its domain. When a domain controller creates a user, group, or computer object, a unique security ID (SID) is assigned to the object. The SID contains two elements:
- One is the domain SID (which is the same name for all SIDs that’s created in a domain)
- And the other is an RID, which is unique for each SID created in the domain.
Activities such as moving an object between domains (using Movetree.exe) must be instigated on the domain controller acting as the RID master of the domain (that currently contains the object).
PDC emulator master
In order to ensure consistency, password changes from client computers must be replicated and updated to all domain controllers throughout the domain. And the PDC emulator can be configured to synchronize with an external time source. Provides consistency in password experience for users across sites. (To turn off use: AvoidPdcOnWan registry parameter). Double-check incorrect passwords and reviews new password changes.
The domain controller configured with the PDC emulator role supports two authentication protocols:
- The Kerberos V5 protocol
- The NTLM protocol
Infrastructure master
Tasks such as updating references from objects in its domain to objects in other domains are under the purview of the infrastructure master. The infrastructure master compares its data with that of a global catalog, which receives regular updates for objects in all domains through replication, thus making the global catalog data up to date.Say, in a scenario where the infrastructure master suspects outdated data, it fetches updated data from the GC and replicates it to the other domain controllers in a domain.
Pointers:
- Unless there is only one domain controller in the domain, the infrastructure master role should not be assigned to the domain controller that is hosting the global catalog.
- If the infrastructure master and global catalog are on the same domain controller, the infrastructure master will not function.
- The infrastructure master will seldom find data that is out of date, so it will never replicate any changes to the other domain controllers in the domain.
- In the case where all of the domain controllers in a domain are also hosting the global catalog, all of the domain controllers will have the current data and it does not matter which domain controller holds the infrastructure master role.
In scenarios where users/members of a group are renamed/modified, the infrastructure master is responsible for revising the group-to-user references.
When the member of a group is moved or renamed, especially if that member resides in a different domain from the group, the member would temporarily not appear in the group. It is the infrastructure master of the group’s domain’s responsibility to update the group of the new name or location of the member. This prevents the loss of group memberships associated with a user account. The update is distributed by the infrastructure via multi-master replication.
Identifying DCs that have been authorized FSMO roles
There are three methods by which you can identify the DC that have FSMO roles.
Method 1:
Go to Command Prompt, and type NetDOM /query FSMO -> Enter
Method 2:
Determining the RID, PDC, and Infrastructure FSMO Holders of a Selected Domain
- Click Start -> Run, type dsa.msc -> click OK.
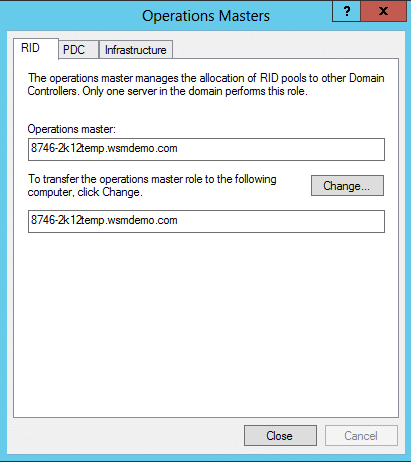
- Right-click the selected Domain Object in the top left pane, and click Operations Masters.
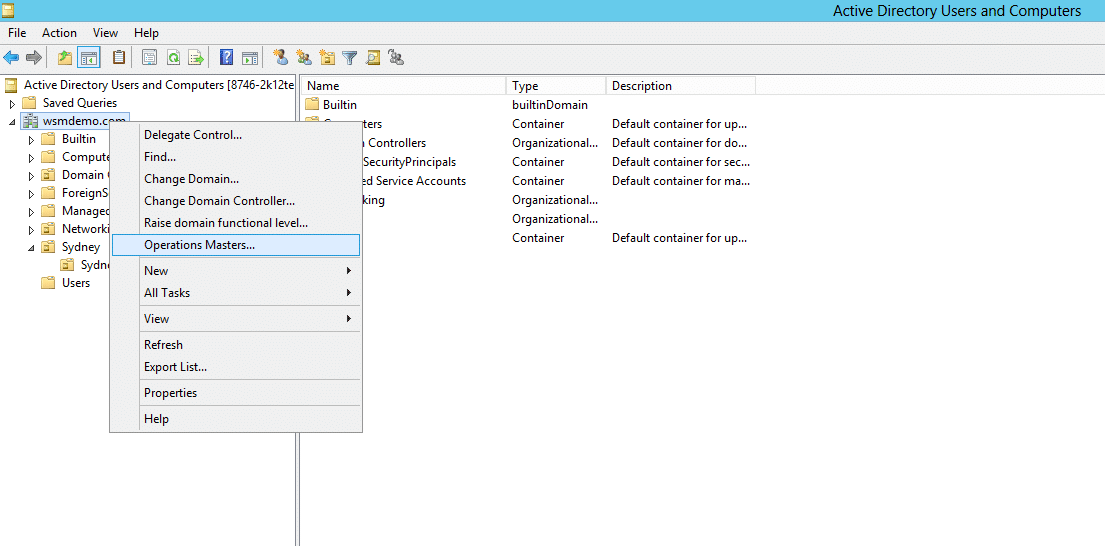
- Click the PDC tab to view the server holding the PDC master role.
- Click the Infrastructure tab to view the server holding the Infrastructure master role.
- Click the RID Pool tab to view the server holding the RID master role.
Determining the Schema FSMO Holder in a Forest
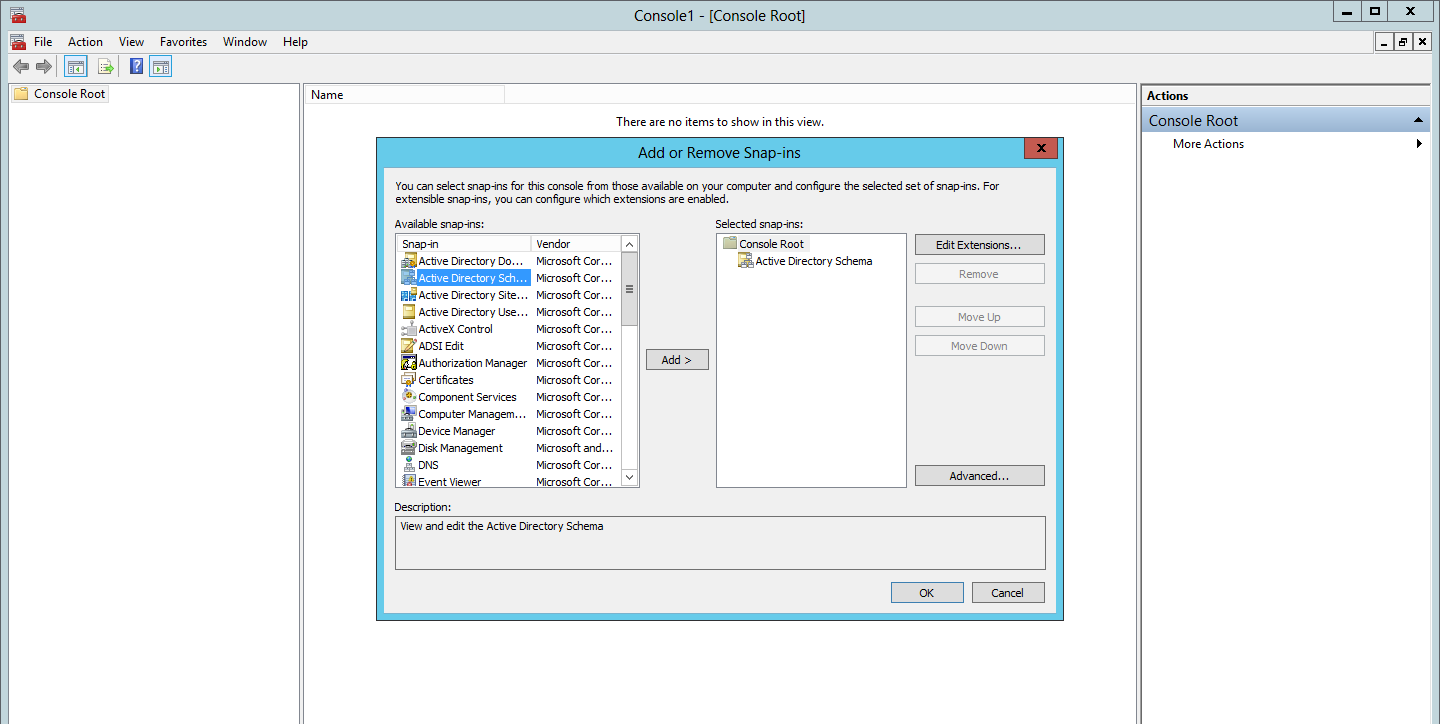
- Click Start -> Run -> type mmc -> click OK.
- On the Console menu, click File -> Add/Remove Snap-in -> click Add -> double-click Active Directory Schema, click OK, and then click Close.
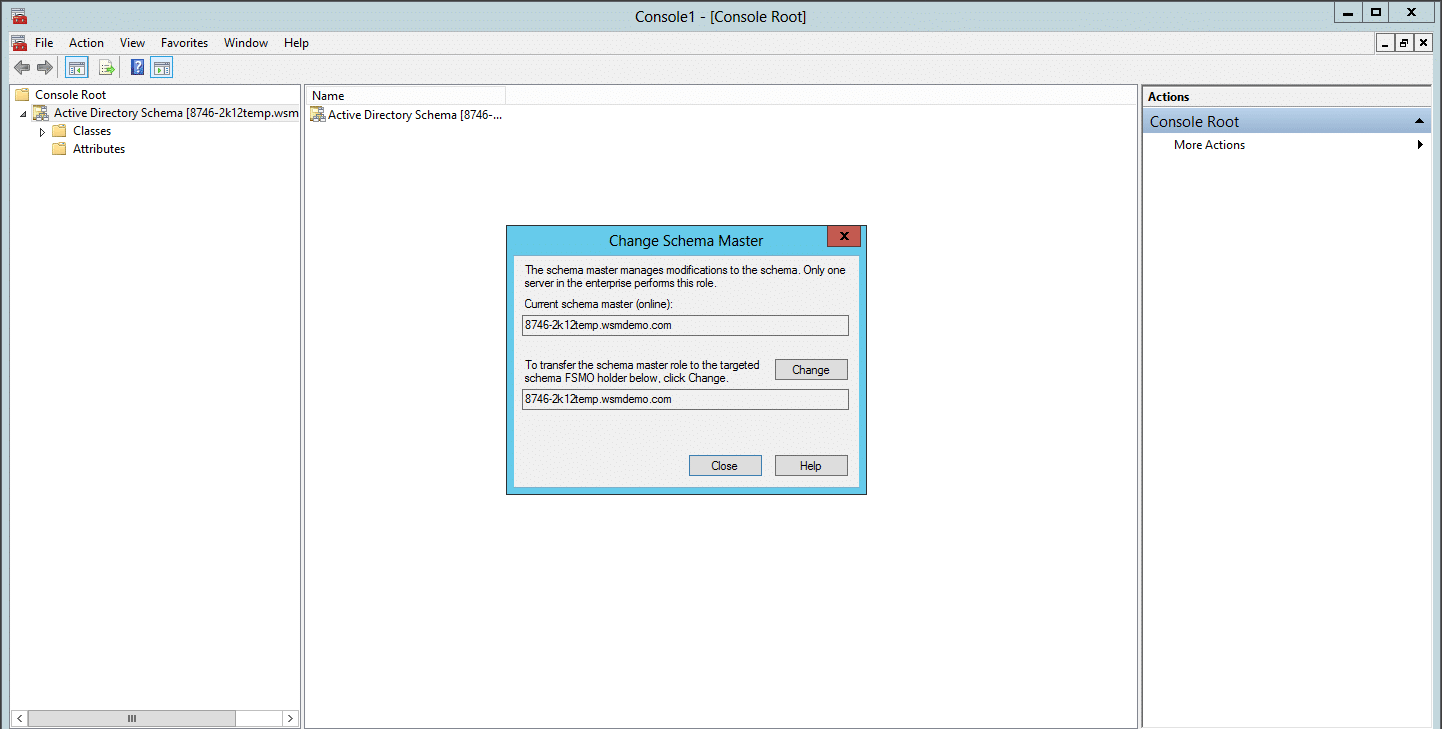
- Right-click Active Directory Schema in the top left pane -> click Operations Masters to view the server holding the schema master role.
Note: For the Active Directory Schema snap-in to be available, you have to register the Schmmgmt.dll file. To do this, you can follow this step:
Click Start -> Run -> type regsvr32 schmmgmt.dll in the Open box -> click OK. A message is displayed that states the registration was successful.
Determining the Domain Naming FSMO Holder in a Forest
- Click Start -> Run, type mmc -> click OK.
- Click File -> Add/Remove Snap-in -> click Add -> double-click Active Directory Domains and Trusts -> click Close -> click OK.
- In the left pane, click Active Directory Domains and Trusts.
- Right-click Active Directory Domains and Trust, and then click Operations Master to view the server holding the domain naming master role in the Forest.
Method 3:
On any domain controller, perform the following steps:
- Click Start, click Run, type Ntdsutil in the Open box, and then click OK.
- Type roles, and then press ENTER.
- Type connections, and then press ENTER.
- Type connect to server , where “server” is the name of the server you want to use, and then press ENTER.
- At the server connections: prompt, type q, and then press ENTER again.
- At the FSMO maintenance: prompt, type Select operation target, and then press ENTER again.
- At the select operation target: prompt, type List roles for connected server, and then press ENTER again.
- Type q 3 times to exit the Ntdsutil prompt.
NTLM authentication and Kerberos Authentication Protocols Explained







