Active Directory Permissions Explained
Users in an Active Directory (AD) network can gain access to resources of the network, whether they are files and folders, or computers and printers. However, not all users need access to all the resources of the network. This is where AD permissions come into play. AD permissions ensure that users of an AD network only gain access to resources that they need. This prevents misuse of resources inside the network. In this article, we will take a look at what AD permissions are, permission inheritance to child objects, and dive into how to assign permissions in AD using two different methods.
What are Active Directory Permissions?
AD permissions are a set of rules that define how much an object has the authority to view or modify other objects and files in the directory. AD permissions are an important functionality. This is because not all objects would need to access everything in the directory. For example, a salesperson in an organization doesn’t need permission to modify their organization’s entire domain. Such a scenario would prove to be a security hazard because, without AD object and group permissions, any person could potentially leak an organization’s vital information or allow for a system-wide hack. Thus, permissions in AD are a security functionality. AD permissions are object-specific. When you assign permission to a container object, for example, you are given the control to restrict certain objects within the container not to inherit the permissions of the parent container. Such control gives fine-grained permission customization to an administrator using AD permissions. It is called permission inheritance, which will be explained below.
Viewing Object Permissions
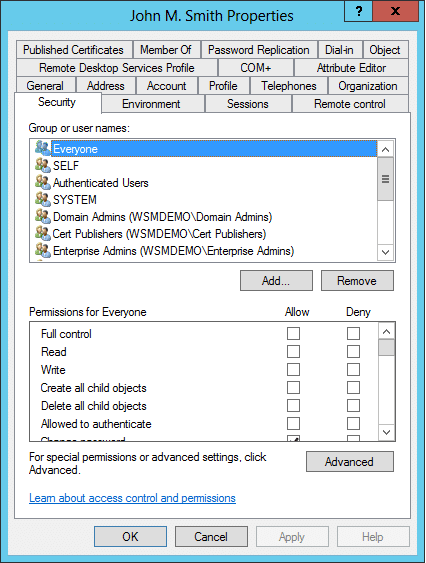
Viewing a user’s permission or an object’s permission can be done through the object’s properties tab. To view the permissions,
- Go to Start, and click Administrative Tools
- Click on Active Directory Users and Computers.
- Locate the object you want, and right-click on it.
- Click Properties.
- Click the Security tab, and you’ll be able to see the object’s permissions.
Modifying Object Permissions
There are two ways to configure AD permissions to objects.
Method 1: By configuring GPOs in the Group Policy Management Console
- Go to Start, and click Administrative Tools
- Click on Group Policy Management
In the console, you can right-click on Group Policy Objects, and click New to create a new GPO. You can then grant the required rights to a set of users/groups through this GPO.
Method 2: Using the Security tab in ADUC
- Go to Start, and click on Administrative Tools
- Click on Active Directory Users and Computers.
- Locate the object you want, and right-click on it.
- Click Properties, and select the Security tab
You’ll be able to see the object’s standard permissions, and you can allow or deny those permissions. For a list of all the object’s permissions, click Advanced in the security tab, and then click Edit to view and modify all the permissions.
Types of Active Directory Permissions
In the Security tab, you will find the basic permissions of the object. This set of permissions are the standard permissions, and they comprise of ‘Full control’, ‘Read’, and ‘Write’ permissions. Some objects, depending on their class, may have additional permissions in the standard section.
However, AD also has a more comprehensive set of permissions called special permissions. These permissions include additional privileges such as ‘modify permissions’, ‘modify owner’, and more. They can be accessed by clicking on Advanced in the Security tab and then clicking Edit. The tab will then show you a list of all the permissions given to the object, and you can modify them. You can either allow or deny these permissions using the check box. You can also define whether the permissions apply only to the object selected, or all its child objects, or just its descendant computer objects, contact objects, or more. This gives you grained control over permissions for not only the selected object but also all objects that come under it.
Object Permissions Inheritance
Permission to an object can be inherited in two ways:
- From the parent object class using which the object was created
- From the group into which the object was placed
When permission is assigned to an object, you can choose whether you want the permission to all its child objects, only a select few, or just the object alone. For example, you have an OU that contains multiple user objects and group objects representing the employees and departments, but there are also several computer objects that are assigned to interns working in your organization. If you want to allow the ‘Delete child objects’ permission to everyone inside the OU except the interns, you can set the permission and choose Descendant group objects in the Applies to section. This will ensure that the permission to delete child objects is given only to the groups within the OU, and not the computers that are outside the groups.
Object Permissions Precedence
Sometimes while setting permissions for objects and their descendants, there are chances where the permission of an object and the container it is in may clash. In such cases, the principle of least privilege is applied. Denied permissions take precedence over allowed permissions. For example:
- John belongs to a group ‘Marketing specialists’.
- John is granted ‘Full control’ permission over a group called ‘Interns’.
- However, the group ‘Marketing specialists’ has been given ‘Read only’ permissions to the interns group.
In this case, John will ultimately be denied the privilege of fully controlling the interns’ group and will only be allowed to read the group.
The principle of least privilege makes sense from a security standpoint, as an object would rather not have the permission it needs, and request for it specifically, than have permission it doesn’t need and then exploit it.
Also, when permission is applied directly to an object, this permission takes precedence over any conflicting permission. Such permissions are called explicit permissions.
Domain Password
Password and account lockout properties for the domain are stored in the Directory Service as attributes of the domain object. These properties can also be managed through the user interface using the Domain Security Policy Group Policy object, the values are then synchronized to the Directory Service. Password policies as well as all account policies are domain-wide and applied to all members of the domain.
People also read