What you will learn:
Active Directory is a powerful directory service that allows organizations to manage all their resources, apply security configurations, and keep everything organized in one place. In this article, we will get an introduction to Active Directory and how it is structured, take a look at the five services of Active Directory, and then dive into what are workgroups, domains, and the difference between these two.
What is Active Directory
Active Directory is a directory service provided by Microsoft. A directory service is a hierarchical arrangement of resources that are structured in a way that makes accessing them easy. However, functioning as a locator service is not AD’s exclusive purpose. It also helps organizations have a central administration over all the activities carried out in their networks.
Organizations primarily use Active Directory to perform authentication and authorization. It is a central database that is contacted before a user identity is verified and granted access to a resource or a service. Once the authenticity of the user is verified, Active Directory helps in determining if the user is authorized to use that particular resource or service. If the user checks out on both counts, access is granted. You can learn more about the basics of Active Directory in this article.
The five services of Active Directory
Active Directory (AD) is a set of five services that run on a Windows server to manage permissions and access to network resources. These five services are:
- AD Domain Services (AD DS)
- AD Lightweight Directory Services (AD LDS)
- AD Federation Services (AD FS)
- AD Certificate Services (AD CS)
- AD Rights Management Services (AD RMS)
Active Directory Directory Service in a nutshell
AD DS is commonly referred to as AD. AD DS is the most deployed component of AD. In a way, AD DS has become synonymous with AD, and when people speak about AD, they’re usually referring to AD DS. If they want to refer to any of the other four services, they explicitly mention that service by name. AD DS is essentially a service for the storage of information just like a telephone directory. Let’s use the below table to understand how AD DS functions.
| LAST NAME | FIRST NAME | ADDRESS | TELEPHONE NUMBER |
| Burns | Joe | 1 Dorset Place | 804 0650 |
| Adams | Marilyn | 20 Dundurn Street | 391 7683 |
| Rajan | Ranjit | 60 Mistdale Cres | 691 8967 |
Imagine each row in the table as a distinct object with information attributes like last name, first name, address, and phone number. In an AD environment, these distinct objects can be users, computers, groups, printers, and more. Each of these objects has characteristics or pieces of information called object attributes. Both the objects and their attributes are stored in AD. AD is extensible, which means that we can add objects and object attributes to it as and when needed.
Is Active Directory a database or a directory service?
Some people consider AD as a database. After all, you can write data to it, retrieve data from it, and store data in it. However, it’s more of a directory than a database since it’s optimized for read operations rather than write operations. While you can add new data to AD, the existing data usually doesn’t undergo many changes. Furthermore, the data in AD is arranged in a logical and hierarchical manner so that finding information is easy. This is just like how a regular directory book organizes contact information by type of business or in alphabetical order.
Structure of Active Directory
When we deploy AD in an organization, we need to consider two sides of its structure:
- The logical side: This is the hierarchy of objects such as users, computers, groups, and organizational units. The AD administrator needs to design a logical side that closely mimics how the organization functions and helps them effectively manage their IT infrastructure. Arranging these various objects in a logic that is efficient helps administrators to easily manage permissions (access) and security.
- The physical side: When designing the physical side, the administrator needs to consider the servers that provide AD services and contain all the critical directory information. They need to answer questions such as:
- How will these servers speak to each other and share information?
- What network links need to be set up so that remote users can be given access?
- How can users in different locations be directed to the servers?
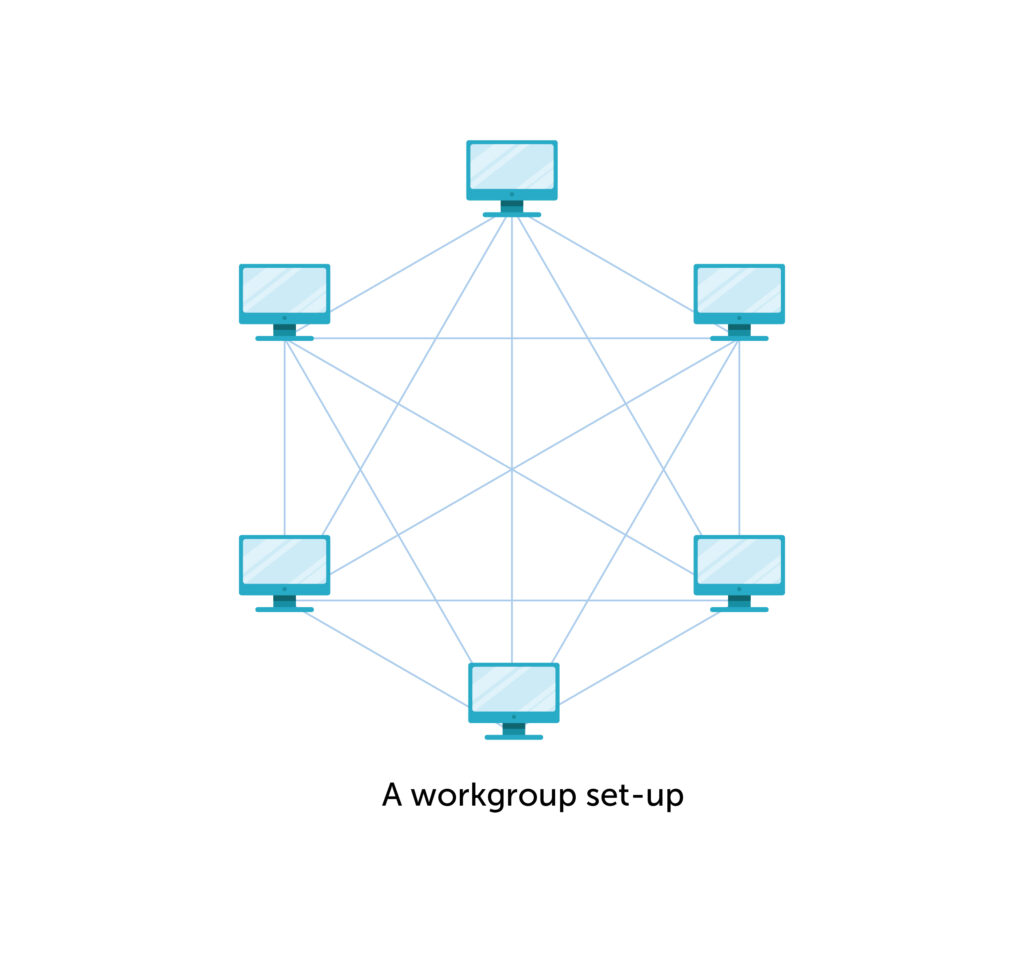
What is a workgroup in Active Directory?
An AD workgroup is a peer-to-peer network with no central authentication. Each computer in a workgroup function as both a client and a server. When a user in an AD workgroup wants to access another user’s computer or even a shared resource like a file, they need to create their username and password on the other user’s computer.
What is a domain in Active Directory?
An AD domain on the other hand comprises computers on a client-server model. The computers are all connected to a central server that provides authentication services. Files and folders are also stored centrally so a user can access those files from any computer.
Workgroup vs domain
Workgroups are great for small office networks with 15 or fewer computers. However, they aren’t ideal for larger companies with hundreds or thousands of users, as it will become difficult to access files and folders of one computer with another computer. Simply put, AD workgroups are fine for small offices, but they are not efficient in scaling to big organizations.
So, for big environments, we need to set up a client-server network environment. In Windows, this is achieved by setting up domains. The domain setup ensures better security as we can give varying degrees of permissions for different users or groups of users. Furthermore, we can deploy company-wide policies for easier administration in a domain than a workgroup.
In an AD domain, all login and access requests by users are managed by a domain controller (DC) that runs AD. A DC is a centralized server that responds to all such requests and is effectively a security gatekeeper for the network. Both authentication and authorization are done by the DC.
- Authentication: The client and server authenticate each other to verify who the user or computer is.
- Authorization: The server determines if the client has the required permissions to access a resource.
Authentication is done through usernames and passwords (along with a process of encryption). The DC will check in its AD database to authenticate users requesting access to the domain. If the user’s credentials match the information contained in AD, they are allowed to log on to the network. Authentication is completed using the Kerberos authentication protocol. Authorization is done through Access Control Lists (ACLs). An ACL is a list of permissions attached to an object and it also specifies which users are allowed access to the object, and what operations they can do. You can learn more about authorization and authentication in this article.