NTLM authentication and Kerberos Authentication Protocols Explained
What you will learn: A network needs to have security processes put in place to avoid the misuse of its resources. An authentication process goes a big way in identifying whether a person is who

Active Directory Maintenance Checklist
What you will learn from this article: There are so many moving parts related to Active Directory (AD). So, it is important to know how to monitor, report, fix and diagnose issues related to the

Group Policy Backup
What you will learn: Group policies are critical pieces of instructions in an Active Directory environment used to configure a variety of advanced settings that can be applied to objects in the network. A set
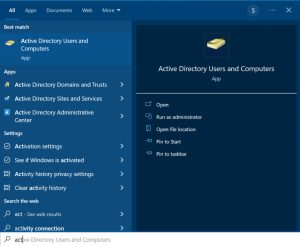
Active Directory Users and Computers (ADUC) – An introduction and installation guide
Active Directory Users and Computers (ADUC) is a common tool used by administrators to carry out daily tasks and much more in Active Directory AD. Some of the tasks an administrator can perform with the
Active Directory Users and Computers (ADUC) – Part II
In part I of Active Directory Users and Computers, we introduced the Active Directory Users and Computers (ADUC) snap-in. We also saw a list of tasks an administrator can perform from the ADUC console and described
Hyper-V Virtualization: An explanation
What you will learn from this article: There are many scenarios where something would need to be tested on a server or a computer machine. In such scenarios, instead of using a physical test machine,
Active Directory Rights Management Services (AD RMS)
What is Active Directory Rights Management Services? Sensitive information in an Active Directory environment can cause a great deal of trouble if it reaches the wrong hands. Every organization should do all in its power to avoid

Security Account Manager (SAM)
What is the Security Account Manager (SAM)? When you log in to your Windows Operating System, you must enter a password to gain access to the system. Have you ever wondered where your passwords are stored when

What is Active Directory?
Large organizations depend on Windows Active Directory (AD) to maintain order in the chaos that is managing users, computers, permissions, and file servers. The sheer number of articles available on the internet can disconcert beginners and
Comparison of Active Directory and Windows NT
Difference between Active Directory and Windows NT What you will learn: Windows NT and Active Directory, at the core, are network operating systems (NOS) developed by Microsoft for centralized management of network devices. Active Directory
Active Directory Objects List
What are objects in Active Directory? Objects in Active Directory (AD) are entities that represent resources that are present in the AD network. These resources can be users, computers, printers, contact persons who may be
User authentication and user authorization process: An explanation
What you’ll learn: Active Directory authentication and authorization are security processes. These processes are necessary in any environment so that the resources of an environment are not misused by anyone. In this article, we will
Benefits of Active Directory
What is Active Directory Active Directory (AD) is a directory service provided by Microsoft designed for Windows domain networks to organize and manage users, attributes, memberships, accounts, and more. It offers centralized authorization and authentication
An Introduction to Lightweight Directory Access Protocol (LDAP)
What is LDAP? The Lightweight Directory Access Protocol, commonly known as LDAP, is a communication protocol used to access directory servers. In other words, LDAP is used to store, update and retrieve data from a
DNS and Active Directory
Domain Name System (DNS) is a name resolution method that is used to resolve host names to IP addresses. It is used on TCP/IP networks and across the internet. DNS is a namespace. Active Directory
Authentication vs authorization process: An explanation
What you’ll learn: Active Directory authentication and authorization are security processes. These processes are necessary for any environment so that the resources of an environment are not misused by anyone. In this article, we will
Active Directory FSMO Roles Explained
What you will learn from this article: Active Directory (AD) relies on the AD replication process to keep the information updated across all its domain controllers (DC) in the network. This replication is done through
What is Global Catalog Server in Active Directory?
What you will learn from this article: An Active Directory network would be made of forests and domains. The domain controllers (DC) of a particular domain would contain all the information of the domain they
What are Domain Controllers?
What are Domain Controllers (DC)? The computer machines that function as servers in the domain can either be a member server or a DC. A member server belongs to a particular domain, but it does
Trusts in Active Directory: An overview
What you will learn from this article: An Active Directory network may contain several domains in a hierarchical fashion. All the resources of one domain are not directly available to every other domain. The availability
Framework of Active Directory
The Active Directory structure is built on the domain level. The framework that holds the objects can be viewed at different levels namely forest, domain trees and domains. At the top of the level is
Active Directory Nested Groups Explained
What you will learn: Nesting groups in Active Directory (AD) allow for better control in managing access to resources in the AD network. Group nesting also makes it easier to assign permissions across multiple domains
Active Directory objects: All you need to know
What you’ll learn: Active Directory (AD) is a directory service introduced by Microsoft as a centralized network resource management system. This network is comprised of entities that represent real users or network resources, and the
Creating objects in active directory
You can create objects in Active Directory by using the Active directory users and computers console. Start -> Administrators tools -> Active Directory users and computers. On the Active Directory users and computers console, right click
Active Directory Subnets, Sites, and Site links
Active Directory Subnets A single, physical network can be broken into smaller segments called subnets in a process called subnetting. Each subnet on a network is connected by routers. Every device in a network, whether
What is a Read Only Domain Controller (RODC)
Introduction A read only domain controller (RODC) is a type of domain controller that has read-only partitions of Active Directory Domain Services (AD DS) database. RODC is available in Windows server 2008 OS and in
Active Directory Schema: An overview into Schema Extension
Active Directory (AD) schema is a blueprint that describes the rules about the type of objects that can be stored in the AD as well as the attributes related to these objects. The schema thus
The structures and benefits of organizational units
Organizational units (OUs) When you deploy Active Directory (AD) in your company, you may decide to create multiple organizational units (OUs) within your domain. An OU is a container within your domain that holds users,
What are Domain Functional Levels and how do you raise them?
Domain Functional Levels – An overview Domain functional level (DFL) determines the features of a Domain Controller (DC) based on the Windows Server Operating System (OS) it runs on. A feature set of a particular
What is a workgroup and how is it set up?
Authenticating users in a computer network. Employees in any organization, big or small, need to log in to their computers at the start of their work day. Logging in gives them access to shared files,
Difference between Disabled, Expired and Locked Account
Introduction: The process of administering and monitoring the activities of the Active Directory service, which is typically found in Windows Server operating systems, is known as Active Directory management. The major goal of AD management
Access Control List (ACLs) and Access Control Entries (ACEs)
What you will learn: In this article, we will take a look at what an access control list (ACL) and an access control entry (ACE) are, the components that make up an ACL and ACE,
Understanding Active Directory Tombstone
What are Tombstones in Active Directory? When you delete an object from the Active Directory (AD) database, it’s marked as a tombstone object instead of being fully removed. By default, each tombstone object remains in
Active Directory Replication: What it is and how it works
What you will learn from this article? Information in the Active Directory (AD) network is modified or updated constantly. In such cases, if any information is updated in one domain controller (DC) of the AD
Active Directory Recycle Bin
What is Active Directory Recycle Bin? The Active Directory Recycle Bin feature allows administrators to restore deleted AD objects. In Active Directory, objects such as users, computers, groups, or organizational units may be unintentionally removed.
Read only domain controller
Introduction A read only domain controller (RODC) is a type of domain controller that has read-only partitions of Active Directory Domain Services (AD DS) database. RODC is available in Windows server 2008 OS and in
Microsoft Passport
Introduction Using passwords is a common approach to protecting and securing a resource from unauthorized access. However, the use and maintenance of passwords have their shortcomings. One challenge is the difficulty of remembering passwords, more so,
Active Directory Certificate Services
What you will learn from this article Before we delve into the Active Directory Certificate Services, let us understand certificates. A digital certificate and a traditional certificate have quite a few similarities. The certificates contain
Microsoft Hello
For quite a long time, we have been following the routine of typing in a password for accessing our computers. Strong password requirements make us set complex passwords which we often tend to forget, and then
DNS and Active Directory
What is AD DNS? Domain Name System (DNS) is a name resolution method that is used to resolve hostnames to IP addresses. It is used on TCP/IP networks and across the internet. DNS is a
Active Directory Basics: Everything you need to know
What you will learn: An organization will consist of multiple employees, devices, contacts, and large amounts of data. It would need to sort all these resources and information in a structured manner for easy access,
What is Azure Active Directory?
Azure Active Directory: Introduction Azure Active Directory is a multi-tenant, cloud-based directory and identity management service provided by Microsoft. It offers identity and access capabilities for applications running in both Microsoft Azure and in an
Active Directory Groups: An explanation
What are Active Directory groups? Active Directory is a Microsoft technology that is used to implement directory services. It is a feature of the Windows Server and one of the most popular on-premise directory services,
Migrating AD from Windows Server 2003 to Windows Server 2016
Active Directory (AD), a service provided by Microsoft, functions as a central database for securely storing and managing information about user accounts, groups, applications, and other critical resources. It primarily functions as a directory service
Integrating AD with LDAP
Introduction Active Directory (AD) is a directory service that stores information about objects on the network in a logical and hierarchical manner. Administrators control and manage access to network resources based on the permissions assigned
Managing shared resources
Introduction When sharing resources in a common network, the biggest concern is delegating access levels to those resources. Permissions management is a critical security process since any pitfalls can make the organizations prone to data

The OSI model: What it is and how you can use it
Developed by the International Organization for Standardization (ISO) in 1984 when network computing was at its nascent stage, the Open Systems Interconnection (OSI) model is the visual representation of how information interacts with different mediums—hardware
How to resolve an AD account lockout issue
Have you ever been frustrated why your account is getting locked out frequently in active directory? If your AD account keeps getting locked out, then you have come to the right place. Account lockouts are
How to install the PowerShell Active Directory module
The Active Directory PowerShell module is part of the Remote Server Administration Tools (RSAT) in all Windows Operating Systems. It is a set of PowerShell cmdlets that imparts flexibility in managing Active Directory. While AD management
Securing administrator accounts in Active Directory
Administrator accounts are the most critical and powerful accounts in operating systems, devices, and Active Directory. Administrator accounts have complete access to all the files, domains, and services on a local server. They are used
How to change the NTFS and share permissions
New Technology File System (NTFS) is the standard file management system provided by Microsoft. Access to any data stored in the NTFS is governed by NTFS permissions. Share permissions govern access to folders shared over a network. It’s not possible to modify permissions for the subfolders or objects in a particular share because these permissions are commonly applied to all its files and folders. Watch this video where we show how you can change the NTFS and share permissions.
Check out a more detailed explanation in our article here 👇
https://www.windows-active-directory.com/managing-shared-resources.html
For more such articles on managing shared resources, visit our website 👇
https://www.windows-active-directory.com/
To stay updated about industry trends and Active Directory best practices, subscribe to our monthly newsletter👇
https://www.manageengine.com/active-directory-360/iamroundup-newsletter.html
#NTFS #shared #windows #activedirectory
How to transfer FSMO roles
What is FSMO? A flexible single-master operation (FSMO) is a set of AD (Active Directory) operations or roles designed to help eliminate replication conflicts. FSMO is used when standard data transfer and update methods are
How to seize FSMO roles
It is a reasonably simple operation to move one or more FSMO roles from one Domain Controller to another. However, given that all DCs are functioning properly and are online. Learn more about FSMO roles
Active Directory LDAP Field – Attribute Mappings
While accessing Active Directory users and computers (ADUC), it can be observed that Microsoft has used user-friendly names for the input fields. These fields are mapped to the LDAP (Lightweight Directory Access Protocol) attributes. You
How to change the IP address of a domain controller
The domain controller (DC) is an integral part of your IT infrastructure. Due to its role within the domain, it’s crucial that any change to its IP is done correctly. The DC’s address is statically
How to quickly check windows server uptime
Windows Server Uptime is a crucial metric to measure the stability and reliability of a server. It shows how long the server has been running without any interruption. In this article, you will learn how
Removing an Exchange Server Mailbox from your environment
An Exchange server is Microsoft’s on-premises mail and calendar offering that allows organizations to streamline effective communication amongst employees. You will be required to remove Exchange Server Mailbox for the below reasons: When an organization

Before migrating to Active Directory Domain Services (AD DS) 2022
In today’s dynamic IT landscape, the need for organizations to be agile and adaptable is more pronounced than ever. Active Directory Domain Services (AD DS) stands as the cornerstone of organizational identity. While the allure
Configure domain password policy – Here’s how
In this article, we delve into configuring the Active Directory Domain password policy, essential for maintaining robust security and compliance within your organization. The following steps, inspired by user interactions and common queries, aim to
Find a user’s last logon time
Ensuring the security and maintenance of Active Directory user accounts is a critical aspect of system administration. One key piece of information is the last logon time for a user, which helps administrators identify inactive
How to create a task via WMI
Creating a task via Windows Management Instrumentation (WMI) involves a series of steps that leverage WMI’s powerful framework for managing Windows-based systems. This article is intended for system administrators and technical professionals who are familiar
WMI classes and categories
Listing every class in Windows Management Instrumentation (WMI) would be extensive, as WMI includes hundreds of classes that cover a wide range of functionalities. However, I can guide you on how to find a comprehensive
How to create a process via WMI remotely
Creating a Remote Process via Windows Management Instrumentation (WMI) In the realm of system administration, the ability to remotely manage and automate tasks on Windows machines is crucial. This article provides a detailed guide on
How to schedule a process remotely via WMI
Remote task scheduling is a critical competency for system administrators managing a network of Windows machines. This article provides a comprehensive guide on how to schedule a process remotely using Windows Management Instrumentation (WMI), without
Configuring Port Forwarding in Windows Using NETSH
Port forwarding is a technique used to direct network traffic from one network port to another. In Windows, the NETSH (Network Shell) command-line tool can be used to set up port forwarding. This article provides
How to raise AD forest functional level
What are Functional Levels? An Active Directory functional level determines what capabilities of Active Directory Domain Services (AD DS) are available for a particular forest or domain. The functional levels are specified in terms of

What is an N-Day Exploit? Definition, Mechanism & Security Risks
An n-day exploit targets a vulnerability after public disclosure, weaponizing the delay between a vendor’s fix and enterprise patch adoption. Definition (snippet-friendly): An n-day exploit is a cyberattack that targets a known software vulnerability after

What’s new in Active Directory (2025): Availability, supportability & security enhancements
Active Directory 2025 security, availability, and supportability are now the defining pillars of enterprise identity resilience. Sneak-peek Here we talk about the latest changes that improve three pillars—availability (staying online), supportability (seeing and fixing issues fast),

Virtualized AD DS Time Sync: A hands-on implementation playbook (VMIC vs AD)
If you run domain controllers as VMs, time is a design decision—not a default. This Virtualized AD DS time sync playbook gives you a clean, production-ready path to make the AD hierarchy your single authority,

Virtualized AD DS time sync: VMIC vs AD — Definitive somparison
Time is the quiet dependency that keeps Active Directory honest. Kerberos tickets rely on it. Replication relies on it. Auditing and security controls rely on it. Virtualization adds the hypervisor’s clock to the mix, creating

Active Directory 25-year evolution: what changed, what stayed true, and what comes next
Comparative guide AD modernization Hybrid identity Zero trust Kerberos Forest recovery Classic AD → Modernized AD → Hybrid future From castle-and-moat to zero trust and hybrid identity: the AD journey. Quick jump: definition · core

FSMO placement strategies for hybrid and cloud scenarios
Active Directory • Hybrid architecture In hybrid identity, where some domain controllers live on‑premises and others in Azure, where you place AD’s five operations‑master roles decides authentication speed, change safety, and your failure blast radius.
DNS delegation architectures for multi-forest environments
Architecture • DNS • Active Directory If you run more than one Active Directory forest, DNS is the fabric that lets users, apps, and domain controllers in one forest reliably find resources in another. The
Transitioning AD schema versions safely: runbook & pitfalls
Active Directory The schema is your forest’s data contract. When you raise its version—via adprep or app extensions—you change what can exist and how it behaves. This self-contained guide explains the why, the risks, and

AD high-availability: RODCs and cross-site redundancy
Active Directory high availability Design for the worst day: local logons at branch speed, safe failover by intent—not accident. RODC Sites & Services Next Closest Site Password Replication Policy Definition (snippet-ready): AD high availability with
SID filtering in complex AD layouts: the one-bit boundary that decides what crosses your forest
Quick definition: SID filtering is a trust-side control that removes foreign SIDs—including values in SIDHistory—from a user’s authorization data as it traverses a trust. It prevents privilege escalation by honoring only the SIDs the trusting
Managing AD metadata cleanup post-DC decommission: A Playbook
Active Directory behaves as if that DC never existed. This guide goes beyond “delete in ADUC” and covers DNS SRV/CNAME integrity, KCC recomputation, lingering objects, and RODC specifics. Focus: metadata cleanup Covers: ADUC/ADSS/ntdsutil Also: DNS

Automating inactive user account cleanup: beyond “run a script every 90 days”
A production-grade playbook for hybrid Active Directory and Microsoft Entra ID (Azure AD) inactive user account cleanup: signals, staged actions, reversibility, and governance—backed by copy‑paste runbooks. On this page Quick definition Why the usual approach
Automated topology design for multi-site replication
Multi-site replication fails in two ways: either it is left to “defaults forever” and slowly drifts away from reality, or it is over-engineered into a brittle, hand-tuned maze that only one person understands. Automated topology

Auditing Nested Group Memberships: An Expert Guide
Reading time: ~14–18 min • Last updated: 2025-09-29 Nested groups are convenient, flexible, and dangerously opaque. This guide shows how to audit them properly in Active Directory and Microsoft Entra, with path-aware reporting,

Automate OU cleanup in AD with PowerShell (Expert Guide)
Active Directory · PowerShell automation Automating OU cleanup in Active Directory with PowerShell: the expert’s comparison guide A practical, production-oriented approach to discover, stage, delete, and prune—safely. Short definition for snippets: Automating
DNS delegation architectures for multi-forest environments
Multi-forest Active Directory environments rarely fail because “DNS is down.” They fail because the DNS namespace was delegated without a clear model of authority, replication boundaries, referral behavior, and the operational ownership that follows. Delegation
Leveraging AD improvements for hybrid cloud usage
Hybrid identity is rarely “cloud identity plus legacy AD.” In most enterprises, Active Directory (AD DS) remains the authoritative source for many user and computer identities, authentication policies, and operational workflows—while cloud services depend
How to enforce policy changes with minimal topology disruption
Enforcing policy changes with minimal topology disruption In Active Directory, “policy change” usually means Group Policy, security baselines, authentication hardening, and configuration shifts that must apply consistently. “Topology disruption” is what happens when enforcement is
AD behind Zero Trust: Asset mapping strategies
Zero Trust fails in predictable ways when the organization can’t answer basic questions like: “What assets exist, who touches them, and what paths connect them?” In enterprises that still run Active Directory Domain Services
Principles from Microsoft AD hardening series
Principles from Microsoft’s Active Directory Hardening Guidance Microsoft has published years of Active Directory (AD) security guidance across documents, reference architectures, “security hardening” checklists, and the broader identity security model used for Windows, Entra ID,
How to handle user SID-related tasks
Handling user SID-related tasks: from first principles to field-tested operations Security identifiers (SIDs) are the nucleus of identity and authorization in Windows and Active Directory. Every access check, every token, every ACL decision hinges on
Restricting logon to specific machines
Restricting logon to specific machines means enforcing which Windows computers a given user may sign in to—locally or via Remote Desktop—using Active Directory controls such as userWorkstations (“Log On To…”) and computer-side User Rights
Auditing failed logons and lockouts
<!doctype html> Failed logons and account lockouts are the earliest, loudest signals of identity trouble in a Windows environment. Sometimes that trouble is harmless (a user typing the wrong password). Sometimes it is operational debt
Hwo to implement LAPS for local accounts
<!doctype html> Local administrator accounts are both necessary and dangerous. They are the “break glass” lever for offline recovery and deep troubleshooting, but they also create one of the most reliable paths for lateral movement
How to automate deletion detection with Recycle Bin
Automating deletion detection in recycle bin: expert guide for Windows cleanup at scale The Windows recycle bin was designed as a safety buffer, not a data retention system. Yet in many environments it becomes exactly
Assign home folders dynamically with scripts
A user home folder sounds simple: “give each person a private network location and map it as H:”. In real environments, that “simple” choice becomes a long-running system: identity meets storage, permissions, audits, migrations, quotas,
Risk-based lockout policy tuning
Risk-based lockout policy tuning is the practice of adjusting lockout behavior based on the assessed risk of an authentication attempt, rather than relying on a fixed “X failed passwords = lockout” rule. The goal
LDAP vs PowerShell for modified account reporting
Modified account reporting in Active Directory sounds simple: “Show me which users changed recently.” In practice, it’s one of those tasks where the tool choice quietly determines whether you get a trustworthy report or
Detecting unmanaged accounts via group audit
Detecting unmanaged accounts via group audit means using group membership changes and “who got added where” telemetry to surface identities that operate outside expected governance: accounts not onboarded to PAM, not tied to HR/ITSM
Cross‑forest account sync and SIDHistory handling
<!doctype html> Cross-forest account synchronization is what keeps access working when identities move between Active Directory forests. SIDHistory is the bridge that lets the new account carry the old identity’s rights without forcing a mass
Cleanup automation using Lepide/Netwrix insights
Cleanup Automation Using Lepide and Netwrix Insights “Cleanup” in Active Directory (and adjacent systems like file servers and M365) is rarely a one-time task. It’s an operating model: continuously detect what’s stale or risky, validate
Alerting on ‘password never expires’ violations
<!doctype html> This article explains what the “Password never expires” setting actually means in Active Directory, why it is risky, and how to build reliable detection and alerting with minimal noise. Why this
Ensuring compliance for dormant/shared accounts
Dormant accounts and shared accounts are two of the most common identity-control gaps in Active Directory and hybrid environments. They create audit findings because they weaken accountability (who did what?) and increase attack surface
Aging analysis of user accounts
Aging Analysis of User Accounts A first-principles approach to reducing access risk, cleaning identity sprawl, and improving audit readiness. What “aging analysis” means: Aging analysis is the practice of classifying user accounts by time-based signals

