Short version (for snippets): To block USB storage with Group Policy, open gpmc.msc, create a new GPO, then enable Computer Configuration > Policies > Administrative Templates > System > Removable Storage Access > All Removable Storage Classes: Deny all access, and link the GPO to your target OU. Run gpupdate /force on clients to apply. This denies read/write/execute for removable storage classes but still allows HID devices like keyboards and mice. Source.
Why disabling USB in 2025 is not a one-liner anymore
“Disable USB” used to mean flipping the USBSTOR driver from Start=3 to Start=4. That works on paper; in practice it clashes with endpoint protection, modern device classes (MTP/PTP phones, virtual Ethernet adapters, hardware keys), and BYOD exceptions. You also need rollback, auditing, and a way to allow specific hardware without reopening the floodgates.
The enterprise-ready approach layers controls: removable storage access policies to block use, device installation restrictions to prevent new installs, exceptions by class or device instance ID, and auditing to prove control. For cloud-managed fleets, pair or replace GPO with Intune or Defender for Endpoint device control for serial-number-level whitelisting and richer reporting. See Microsoft’s guidance on Defender device control and Intune’s USB restriction settings.
What the basic view gets wrong
The surface view is: “Turn on All Removable Storage Classes: Deny all access and done.” That’s incomplete because:
- It blocks use but not necessarily installation of new device drivers.
- It may interfere with legitimate workflows (e.g., camera ingestion, approved encrypted sticks) unless you add precise exceptions.
- It does not produce compliance artifacts by itself—auditors still ask for event trails.
- USB isn’t just storage: think HID, serial adapters, USB tethering, and network class devices.
First principles: how Windows decides whether a USB device works
Four levers govern the outcome when a user plugs a USB device:
- Driver availability and start state. If the storage class driver (
USBSTOR) is present and enabled (Start=3), Windows can mount mass storage. If set to4, storage won’t start. This is the coarse “nuclear” switch and can be toggled by GPO/registry. See Windows OS Hub and Microsoft Q&A on theUSBSTORvalue behavior. - Removable storage access policies. Under Removable Storage Access, Windows enforces read/write/execute denies per class (e.g., all removable storage classes). This blocks access even if the driver loads. See ADMX_RemovableStorage CSP for policy semantics.
- Device installation restrictions. These GPOs determine whether a device can be installed by class GUID, hardware ID, or instance ID. Use them to prevent installation of new USB storage while allowing HID classes. See Manage device installation with Group Policy.
- Security filtering and scope. Who and what gets the GPO? Where in the OU tree? Loopback? These determine “blast radius,” exemptions, and order of precedence.
Approach comparison at a glance
- GPO – Removable Storage Access: Fast, domain-native, blocks use; coarse exceptions by class are limited. Good baseline. Example.
- GPO – Device Installation Restrictions: Prevents new installs; supports allow/deny by class and device IDs; combine with storage access for defense in depth. MS Docs.
- Registry (
USBSTOR): Coarse kill-switch; least flexible; sometimes flipped back by management tools or drivers. Not recommended alone. MS Q&A. - Intune settings catalog: Cloud-managed, supports allow-lists by class/ID; pairs with compliance and reporting. MS Docs.
- Defender for Endpoint device control: Policy + audit + optional serial-based allow lists; cross-platform; best for high-assurance programs. MS Docs.
Hero section — the complete technical rollout (tested pattern)
The steps below assume a Windows AD domain, a pilot OU, and configuration management discipline (change tickets, rollback). They synthesize Microsoft guidance, practitioner notes, and the realities discussed in forums like r/sysadmin and Microsoft Q&A.
0) Pre-flight checks (don’t skip)
- Inventory device classes you must allow: keyboards, mice, webcams, headsets, smartcard readers, hardware keys (FIDO), trusted encrypted sticks.
- Identify risky classes to block: disk drives, WPD (MTP/PTP phones), USB network adapters, USB serial adapters.
- Document affected OUs and build an “Exceptions – USB Allowed” AD group for surgical whitelisting.
- Decide on enforcement order: Access Deny first, then Install Restrict, then optional USBSTOR kill-switch for kiosks.
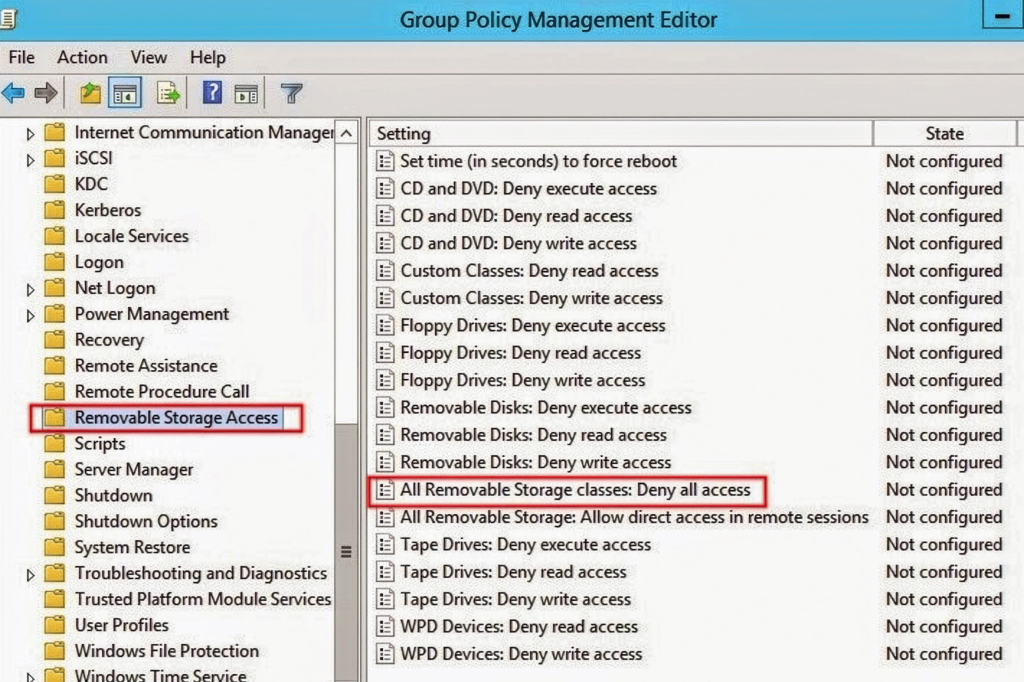
1) Block removable storage access via GPO (baseline)
- Open Group Policy Management (
gpmc.msc) and create a new GPO, e.g., “USB – Deny Removable Storage”. Ref. - Edit the GPO: navigate to Computer Configuration > Policies > Administrative Templates > System > Removable Storage Access.
- Enable All Removable Storage Classes: Deny all access. This denies read/write/execute to ALL removable storage class drivers. See Windows OS Hub and Microsoft’s ADMX CSP reference here.
- Link the GPO to your Pilot – Workstations OU.
- On a pilot client, run:
gpupdate /force ``` gpresult /h %TEMP%\usb-gpo.html && start %TEMP%\usb-gpo.html - Validate: plug in a USB stick. You should see “Access is denied” and file system not mountable even though devices enumerate.
2) Prevent installation of new storage devices (defense in depth)
- Create a GPO “USB – Block New Installs (Device Install Restrictions)”.
- Navigate to Computer Configuration > Policies > Administrative Templates > System > Device Installation > Device Installation Restrictions. See Microsoft’s step-by-step.
- Enable:
- Prevent installation of devices not described by other policy settings = Enabled.
- Allow installation of devices that match any of these device IDs = Enabled (for specific whitelisting later).
- Allow installation of devices using drivers that match these device setup classes = Enabled (add allowed class GUIDs).
- Display a custom message title/text when device installation is prevented (user feedback helps).
- Add allowed class GUIDs for essentials (per Microsoft’s class list). Examples:
- Keyboard:
{4d36e96b-e325-11ce-bfc1-08002be10318} - Mouse:
{4d36e96f-e325-11ce-bfc1-08002be10318} - HID:
{745a17a0-74d3-11d0-b6fe-00a0c90f57da}
- Keyboard:
- Block storage classes implicitly by not allowing them, or explicitly via Prevent installation of devices using drivers that match these device setup classes with DiskDrive
{4d36e967-e325-11ce-bfc1-08002be10318}and WPD (imaging/portable devices) classes from Microsoft’s list. - Link to pilot OU, update, and test by plugging a new USB stick that was never installed on the machine. You should see a block with your custom message.
3) Surgical exceptions (whitelist by device instance ID)
When a team needs a specific encrypted stick or a vendor dongle, don’t relax global policy. Allow just that device instance ID.
- On a lab machine where the device is temporarily allowed, capture its instance path:
```# Option A: PowerShell ``` Get-PnpDevice | Where-Object {$_.Class -in @('USB','DiskDrive','WPD')} | Get-PnpDeviceProperty DEVPKEY_Device_InstanceId | Select-Object InstanceId, KeyName, Data # Option B: Device Manager > Properties > Details > Device instance path - In the USB – Block New Installs GPO, add the captured device instance IDs under Allow installation of devices that match these device IDs.
- Optionally, pair this with Removable Storage Access Read-only exceptions if the policy model requires read-only sticks.
- Document the exception owner and expiry date.
Forum practitioners often recommend moving whitelisting and auditing to the EDR level (e.g., serial-number allow lists in CrowdStrike/Carbon Black). See this discussion in r/sysadmin.
4) Optional: disable the USB mass storage driver
For kiosks, manufacturing floors, or highly locked-down systems, flip the USBSTOR driver to disabled via GPO preferences or startup script:
reg add "HKLM\SYSTEM\CurrentControlSet\Services\USBSTOR" /v Start /t REG_DWORD /d 4 /fThis is coarse and can be reverted by management agents or updates. Use it as a belt-and-suspenders to the above policies, not as your only control. See Microsoft Q&A notes and practical write-ups like Windows OS Hub.
5) Validation and audit (prove it works)
- Generate RSOP:
gpresult /h %TEMP%\rsop-usb.html && start %TEMP%\rsop-usb.html - Audit removable storage and PnP activity. At minimum enable:
- Advanced Audit Policy → Object Access > Removable Storage (Success/Failure).
- Advanced Audit Policy → Detailed Tracking > PNP Activity (Success/Failure).
- Optionally integrate Defender for Endpoint device control for policy/reporting and serial-based allow lists.
6) Rollout strategy and blast-radius control
- Start with a pilot OU containing IT and power users who can validate exceptions.
- Use security filtering so only a scoped group receives the GPO initially.
- Roll out to broader OUs once exceptions are stable. Consider separate GPOs per class (storage vs. WPD vs. USB NICs) to ease future adjustments.
- For VDI, consider loopback (replace) and specific broker OU scoping.
Implications, gotchas, and silent dependencies
- Existing vs. new devices. “Prevent installation of devices not described …” stops new installs. Already installed devices may continue to work unless you remove them or also deny access. That’s why we pair access denies with install blocks. See Microsoft’s device installation guide here.
- Phones and cameras aren’t “disk drives.” MTP/PTP uses WPD/Imaging classes. Block those too if data egress via phones matters. Microsoft’s Intune page lists common GUIDs (HID, imaging, cameras, etc.) for allow lists here.
- USB network adapters. A USB Ethernet/Wi-Fi dongle can bypass your NAC if allowed. Treat network class devices as “deny unless” and allow only corporate-issued models via instance ID.
- EDR conflicts. Some EDR/AV solutions include their own device control. Clarify precedence and avoid dueling user experiences.
- Registry flips don’t age well. Admins report the
USBSTORStartvalue being reset by updates or tools; rely on policy not ad-hoc registry when possible (see user experiences in Super User / ElevenForum).
Mental models experts use
- Separate “use” from “install.” Denying access ≠ preventing driver install. To close gaps, implement both layers.
- Allow-list to minimal viable classes. Only add class GUIDs you absolutely need (HID, system). Everything else gets blocked unless explicitly allowed by device ID.
- Exceptions are per-device, not per-person. When someone needs access, permit that hardware (instance ID), then assign device custody to a team or locker.
- Audit is a feature, not an afterthought. If you can’t prove it in logs and reports, assume it didn’t happen. Bake in RSOP and event checks in your change template.
Misunderstandings, risks, and the fixes
- “All Removable Storage: Deny all access will block everything USB.” False. HID keeps working; phones might still enumerate under WPD unless you block those classes. Fix: explicitly review class coverage (DiskDrive, WPD, Imaging, USB network).
- “We can just flip USBSTOR in the registry.” Risky. It’s coarse, reversible by agents or updates, and not auditable. Fix: use GPOs for access and installation, registry only for kiosks with documentation.
- “We can whitelist by vendor ID.” Too broad—any device from that vendor gets in. Fix: prefer instance ID or EDR serial allow list.
- “We don’t need user messaging.” Wrong. Without a custom deny message, help desks get tickets. Fix: set the custom text/title in installation restriction policies.
Expert essentials (checklist)
- Baseline: enable All Removable Storage Classes: Deny all access on workstations.
- Add device installation restrictions: allow HID classes; prevent anything not explicitly allowed.
- Whitelist by device instance ID only; log owner and expiry.
- Enable audit categories: Removable Storage + PNP Activity; keep RSOP reports.
- Stage rollout via pilot OU; use security filtering.
- Consider Defender for Endpoint device control or Intune for advanced allow-lists and reporting.
How this compares to Intune and Defender for Endpoint device control
Group Policy is perfect for domain-joined, network-reliant machines; you can get very far with access deny + install restrict. Intune shines for internet-first devices and mixed fleets, using the settings catalog to block by class and allow by hardware IDs, with policy variance by user groups (MS Docs, plus practical walkthroughs like Prajwal Desai and TechPress).
Defender for Endpoint device control adds mature logging, user prompts, and options to allow by serial number across platforms, which practitioners in r/sysadmin repeatedly recommend for tightly controlled exceptions. Microsoft’s overview is here: Device control.
Troubleshooting and validation workflows
Common symptoms
- USB stick mounts read-only — You enabled read deny but not write deny or vice versa. Verify policy combinations under Removable Storage.
- Old sticks still work — Device already installed before you enforced “prevent installation.” Remove the device + driver, then re-test with policy in place.
- Phone shows up as “Portable device” and transfers photos. Block WPD / imaging classes, not just DiskDrive.
- Drivers still attempt to install — You configured access deny but not install restriction.
Quick commands
# List installed storage-like devices
```
Get-PnpDevice -Class DiskDrive, WPD, USB | Format-Table -Auto
# Show device instance ID for a specific device (plug it in first)
Get-PnpDevice | ? { $_.FriendlyName -match 'USB|Disk|Portable' } |
Get-PnpDeviceProperty DEVPKEY_Device_InstanceId |
Select-Object InstanceId, Data
# Remove an installed USB storage device (forces re-eval of policy on next plug)
pnputil /remove-device ""
# Confirm applied GPOs and settings
gpresult /h %TEMP%\gpo-usb.html && start %TEMP%\gpo-usb.htmlSecurity operations: audit events and reporting
To satisfy audits, pair GPO with logging. Enable Object Access > Removable Storage and Detailed Tracking > PNP Activity. For friendlier reporting, consider ADAudit Plus’ removable storage reports which draw on those categories and expose who/what/when/where dashboards. Their guide outlines the exact audit categories you should toggle (ref, downloadable PDF here).
Policy patterns you can copy
“Block everything except HID” (workstations)
- Removable Storage Access: All Removable Storage Classes: Deny all access = Enabled.
- Device Installation Restrictions: Prevent installation of devices not described by other policy settings = Enabled.
- Allow classes: Keyboard, Mouse, HID, System devices.
- Block classes: DiskDrive, WPD/Imaging, USB network.
- Exceptions: Whitelist by instance ID for encrypted sticks used at the help desk.
“Read-only ingest for media teams”
- Removable Storage Access: Deny write/execute for removable storage classes; allow read.
- Device Installation Restrictions: Allow instance IDs of corporate SD card readers.
- User messaging: “Write to external media is disabled. Use the ingest share.”
“Kiosk lockdown”
- All of the above, plus
USBSTORStart=4via startup script. - Block USB network class devices explicitly.
- No exceptions.
When to pick a different tool
If your fleet is hybrid/AADJ, or you need per-serial whitelisting with user prompts, consider:
- Intune settings catalog for blocking and allowing by class/ID with cloud reporting (docs).
- Defender for Endpoint device control for advanced policy and analytics (docs).
- ManageEngine Endpoint Central for USB device restriction and unified endpoint workflows (overview, how-to), and ADAudit Plus for reporting (audit).
Forward look: USB control as part of data loss prevention
USB is one egress vector. The same principles extend to Bluetooth file transfers, cloud sync folders, and print-to-PDF. Your target state should integrate device control with DLP: block unknown storage, watermark exports, and monitor egress channels. Expect more organizations to migrate from “GPO only” to “GPO + EDR device control,” because auditability and per-device exceptions are easier to manage there (r/sysadmin thread).
Key takeaways
- Use two layers: deny access to removable storage and prevent installation of new devices.
- Allow only essential classes (HID, system), whitelist specific hardware by instance ID.
- Prove it with RSOP and audit events; don’t rely on registry toggles alone.
- For modern fleets, consider Intune/Defender for rich policy and reporting.
Appendix: fully worked example (copy/paste)
GPO 1 — USB: Deny Removable Storage
- Create GPO, set scope to pilot OU.
- Enable All Removable Storage Classes: Deny all access.
- Optionally set Deny read and Deny write individually if read-only is desired.
- Validate with
gpresultand test.
GPO 2 — USB: Device Installation Restrictions
- Enable Prevent installation of devices not described by other policy settings.
- Allow classes: Keyboard, Mouse, HID (add class GUIDs as above).
- Custom block message: “USB storage is blocked by policy. Open a ticket for a temporary exception.”
- Add device instance IDs as needed under Allow installation of devices that match these device IDs.
Optional kiosk script
@echo off
```
:: Disable USB Mass Storage driver (coarse lockdown)
reg add "HKLM\SYSTEM\CurrentControlSet\Services\USBSTOR" /v Start /t REG_DWORD /d 4 /f
:: Confirm advanced audit policy categories are enabled via auditpol or GPO
auditpol /get /category:"Object Access"
auditpol /get /category:"Detailed Tracking"References and further reading
- Microsoft Q&A: Block USB storage in a domain
- Windows OS Hub: Disable USB drives using Group Policy
- Device control (Defender for Endpoint): Overview
- Intune USB restrictions: Settings catalog
- Windows device setup class GUIDs: System-defined classes
- Discussion: Blocking USB drives — exceptions?
- ManageEngine (friendly references): Endpoint Central — USB blocking, ADAudit Plus — monitor removable storage
Suggested internal links (windows-active-directory.com)
- Group Policy basics: processing order, scope, loopback
- Device installation restrictions: class vs hardware vs instance IDs
- Advanced audit policy checklist for AD-joined endpoints
- Defender for Endpoint device control: serial whitelisting
- Hardening WPD/MTP/PTP and phone tethering