What is LDAP?
The Lightweight Directory Access Protocol, commonly known as LDAP, is a communication protocol used to access directory servers. In other words, LDAP is used to store, update and retrieve data from a directory structure.
The term “lightweight” is used in comparison with X.500, which was the previous standard for directory services. X.500 was complicated, and it relied on the OSI protocol stack. It could not use the TCP/IP protocol stack. LDAP was hence developed as a lightweight alternative, as it could use the much simpler TCP/IP stack while simplifying and removing some complicated X.500 operations and features. LDAP has become popular owing to the fact that it is a lightweight, open, and cross-platform protocol.
What is LDAP used for?
To understand the services provided by LDAP, it is necessary to understand what a directory is. A directory is a hierarchical database that is used to store and organize information about objects. The information in a directory is read more often than they are written or updated. This is one of the most important characteristics that set directories apart from relational databases. Hence, directories are optimized to respond to high-volume search operations or read requests. A telephone directory or phone book is one of the most common examples that can be used for explaining a directory. Each person is represented using an entry and their contact information is represented using key-value pairs.
LDAP defines a message protocol that is used by directory clients and servers. An LDAP directory can be used to store and access various types of information such as images, text, and binary information. Storage and retrieval of data, authentication of clients, and searching for specific data are some of the services provided by a directory service. It can be used in a large organization consisting of thousands of employees, for storing and maintaining information about the employees and resources. Apart from storing information, a directory service also provides authentication and authorization services for users. An organization can also use LDAP for directory services authentication.
For an organization that operates in different parts of the world, there are hundreds of divisions based on business roles and thousands of employees. Using LDAP, all the employee information can be stored and organized in a directory for easier access. For instance, employees in an organization can be categorized based on their departments such as marketing, sales, HR, or more. Using LDAP, the HR manager can be delegated control to the HR tree, and the other trees can be given control to the respective department managers. If the HR manager wants to access an employee’s record for changing the salary details, the authorization and access are made easier using LDAP.
What is the difference between Active Directory and LDAP?
LDAP is a protocol that forms the basis for different directory services and access management solutions. These directory services understand and use LDAP. Active Directory is a directory services implementation developed by Microsoft that is used to provide services such as authentication, group and user management, policy administration, etc. It is a directory service that supports LDAP, which means directory access in Active Directory is performed by means of LDAP. While Active Directory is just one such example, there are many directory services like OpenLDAP that support the protocol.
Just like how SMTP and IMAP are the protocols that are used to send and receive emails, while Gmail is the email application that uses the protocol. LDAP is a protocol on which Active Directory is based. In simpler terms, just like how SMTP is a way of speaking to the email application, LDAP is a means of speaking to Active Directory.
Directory Structure of LDAP
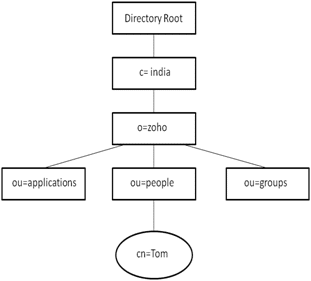
The directory structure can be used to explain how data is stored and accessed in LDAP. Data in LDAP is stored in objects. The objects contain a set of attributes, which are a set of key-value pairs. The set of attributes that an object may contain is defined using a class.
In LDAP, a collection of objects is organized in a hierarchical tree structure called the directory information tree (DIT). It is analogous to a tree with the trunk being the directory root, with the branches and leaves being objects. The tree can contain information in both leaf and non-leaf nodes. The root element is present at the top of the hierarchy, and it is entirely conceptual.
What are the components that make up LDAP?
An LDAP directory information tree (DIT) is made up of several components, listed as follows.
Entries: The objects that make up the DIT are called entries, and they have specific positions within the hierarchy. The objects are of two types:
- Container objects
- Leaf objects
Each entry has three components namely a Distinguished Name (DN), a collection of attributes, and a collection of objects.
Distinguished Name (DN): The Distinguished Name (DN) acts as the unique identifier for each entry. The value of the DN is the position of an object in the tree. It identifies the entry and its position on the Directory Information Tree (DIT). The DN is made up of attribute=value pairs such as:cn=Tom, ou=people, o=zoho, c=india
Attributes: Attributes are used to describe the object and they are defined as key-value pairs. A standard set of attributes are defined according to LDAP specifications that are used commonly. A collection of attributes are used to define an entry. The attributes are defined in a schema. Attribute names are in the form of strings such as, “cn” for common name, “dc” for domain component, “ou” for organizational unit or “mail” for email address.
The Distinguished Names (DNs) are made up of elements called Relative Distinguished Names (RDNs). The RDNs are derived from the attributes of the entries in the LDAP directory. They take the form of <attribute name> = <value>.
Object Classes: A collection of attributes that make up an object class. Associated attributes are grouped together to make it easier to describe things. For example, objectClass: person. Object classes are of two types, namely structural or auxiliary.
Schema: A schema is constructed using objectClass definitions and attribute definitions. It is a set of rules that define the structure of the DIT and the kind of information that the server can hold. Many different schemas can exist for the same DIT.
LDAP Architecture:
As mentioned earlier, LDAP is a communication protocol that is used to define the content of messages exchanged between directory clients and servers. These messages specify the operations that are requested by the client and the responses from the server, including the format of data. Examples of the requested operations include search, modify, add and delete. The messages are carried over the TCP/IP protocol stack.
In the previous example, it was mentioned that the HR Manager wanted to access an employee’s record for changing the salary details. How exaclty does the procedure take place? Here, the Sales Manager is the LDAP client that interacts with the LDAP server.
An interaction between the LDAP client and the LDAP server takes place in the following manner.
- The first step is known as binding, where the client establishes a session with the LDAP server. The client also specifies the host name or IP address and the TCP/IP port number where the server listens.
- The client can then provide a user name and password to the server for authentication, or establish an anonymous session with default access rights. A session with stronger security measures such as data encryption can also be established.
- The client performs operations on the directory data. Read, update and search capabilities are offered by LDAP. Searching is one of the most common operations in LDAP.
- Once the client completes making requests, it closes the session with the server which is known as unbinding.
Thus, the authorized personnel is able to access and modify entries in the directory using the procedure mentioned above.
LDAP Operations:
Some of the operations defined by LDAP for accessing and modifying entries are binding and unbinding, searching, adding and deleting entries, modifying entries and comparing entries.
The basic LDAP operations are described as follows.
- Bind: The LDAP bind operation is used to establish a session between the client and server and to authenticate a user.
- Unbind: The unbind operation is used to close the connection to the server, after the requested operation has been performed.
- Search: The search operation is used to find and retrieve directory entries matching the specified criteria.
- Compare: The compare operation is used to check whether an entry has a specified attribute value.
- Add: The add operation is used for creating new entries in the directory
- Delete: The delete operation is used for removing certain entries from the directory
- Modify: The modify operation is used to change an entry in the directory
- Modify DN: The modify DN operation can be used to change the Distinguished Name of an entry in the directory.
- Abandon: The abandon operation is used to request the server to stop processing an operation which was requested previously.
Extended: This operation is used to request a process that is not defined by any of the other operations.
LDAP Models:
The LDAP models describe the different features of the directory and the services provided by the server. LDAP is based on four models, which are explained as follows:
- Information model
The information model describes the way in which information stored in a directory is structured and organized. An entry is the basic unit of information that is stored in a directory. They are made up of a collection of attributes containing information about the object. Each attribute has a certain number of values, where the kind of values that can be stored is defined by the syntax. For example, entries might be people, organizations or servers and the attributes might be name, telephone number, etc.
- Naming model
The naming model defines the way in which the entries are organized and identified. The entries are organized in a hierarchical tree structure called the Directory Information Tree (DIT). Each entry is identified by a unique name called the Distinguished Name (DN), which is composed of a sequence of Relative Distinguished Names (RDN).
- Functional model
The functional model describes the various functions and operations that can be performed in the LDAP directory. Under this model, the operations are grouped into three categories, based on the functions they are used to perform.
a) Authentication
This includes the operations that are used to establish and terminate connections with an LDAP server. It consists of the Bind, Unbind and Abandon operations.
b) Query
This includes operations that are used to retrieve information from the directory. It consists of the Search and Compare operations.
3) Update
This includes the operations that are used to make changes to the entries stored in the directory. It consists of the Add, Delete, Modify and ModifyDN operations.
- Security model
The security model defines the way in which information in a directory can be protected from unauthorized access. This model is largely based on the Bind operation, which forms an important part of authentication. This operation can be performed in several ways, allowing the security mechanisms to be applied in different ways.
Security and Authentication in LDAP
While managing a directory that contains information about an organization and its employees, security is of great importance. When security mechanisms are not in place, the directory becomes vulnerable to threats from both within and outside the organization. For example, the salary records of an employee should be accessible only to the concerned HR manager. If it was made available to everyone in an organization, the data possess the risk of being tampered with. This is why security mechanisms should be employed. The term security includes aspects such as authentication, authorization, integrity, and confidentiality. Security is maintained in LDAP using the following methods.
- No authentication
This is the simplest method and is supposed to be used only when security is not of much importance. This is used when access control permissions are not required, and if the data can be accessed by anyone. For example, this can be used for a directory where the list of employees in an organization can be accessed by anyone. When the DN and password fields are left empty, an anonymous session is assumed by the LDAP server. Hence the required access control is given to the client.
- Basic authentication
This method provides the basic level of security that is incorporated in web-based protocols. The client is required to provide a DN and password, following which they are authenticated by the server. The problem with using this method is that the password can be read from the network. While this provides the minimum level of security, it is not meant to be used for securing highly confidential information.
- Simple Authentication and Security Layer (SASL)
The SASL is a framework that is used to add additional authentication mechanisms to the connection-oriented protocols. The LDAP version 2 did not support SASL, as a result of which it was added to version 3. Here, the client and server exchange data for authentication, and a security layer is established. Subsequent communication is carried out over this layer. SASL supports pluggable authentication; hence the client and server are allowed to negotiate and use any type of authentication that is required.
LDAP server implementations
Since LDAP is an open protocol, there are several different implementations available. Based on your organization’s requirements you can choose an LDAP server. The administrator or implementer is free to choose the operations of the server, according to their needs. Some of the most commonly used LDAP servers are OpenLDAP, Apache Directory Server, IBM Tivoli Directory Server, Red Hat Directory Servers, and many more.
OpenLDAP is one of the most popular open-source LDAP servers available. Developed for Linux-based systems, it requires a reasonable amount of proficiency and mainly, it functions at the command line. Hence only experienced IT professionals use it.
The Apache Directory Server is another popular implementation of LDAP. It includes support for Kerberos, which is a network authentication protocol. It has better management capabilities with the Apache Directory Studio.