What are Functional Levels?
An Active Directory functional level determines what capabilities of Active Directory Domain Services (AD DS) are available for a particular forest or domain. The functional levels are specified in terms of Windows Server versions, as each version update brings with it a host of new AD DS functionalities. Functional levels have to be specified because their functionalities are not backward compatible with previous functional levels. Let us take a closer look on how to raise forest functional level.
Functional levels are classified into two types:
-
Forest functional level (FFL)
Forest functional level (FFL)
A forest functional level determines the functionalities of AD DS that are enabled in a forest. Raising an FFL increases the capabilities of all the domain controllers (DC) in the forest. For example, Windows Server 2016 brought Privileged Access Management (PAM) functionalities along with all the functionalities of the previous version.
How to check forest functional level?
You can view your forest functional level by following these steps:
-
Go to Start and open Administrative Tools
-
Go to Active Directory Domains and Trusts
-
Right-click on the root domain, and go to Properties
-
Under the General tab, you will be able to see your forest and domain functional levels
Using PowerShell to find the Forest Functional Level
You can find the Forest Functional Level of your domain using the following PowerShell command:Get-ADForest | fl Name,ForestMode
Choosing your forest functional level
When deploying AD DS, you will be given the option to choose your forest functional level. When choosing the forest functional level, do note that the domain functional level should be the same as the forest functional level or higher. Any new domain that is added to this forest will take the forest functional level by default.
How to raise forest functional level
If at any point, you need to change the functional level of your forest, you can do so by following the steps given below. For example, if you want to raise forest functional level from 2012R2 to 2016, here’s how you can do it:
-
Go to Start and open Administrative Tools
-
Go to Active Directory Domains and Trusts
-
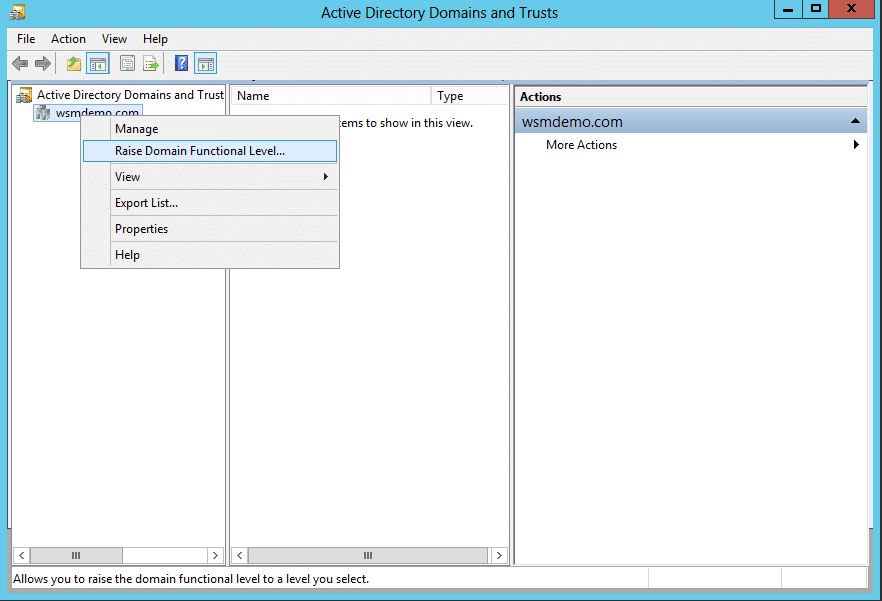
In the left pane, right-click on Active Directory Domains and Trusts and select Raise Forest Functional Level.
-
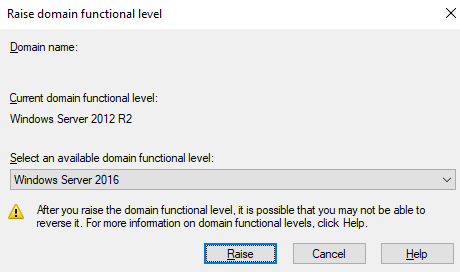
You will see a list of forest functional levels that are available. Select the required functional level. In this case, select Windows Server 2016.
-
Click Raise.
-
You will get a warning message. Read the message, and click OK.
-
Click OK on the confirmation dialogue box.
Things to note before raising your forest functional level
Raising your forest functional level gives your forest access to new and improved AD DS functionalities. However, there are also certain things to take care of before raising the functional level, so that all systems remain functional.
Firstly, you will have to ensure that all the DCs in the forest are running the same Windows server version as the forest functional level you intend to have, or higher. If not, identify those DCs, and either upgrade their Windows Server versions or demote them as necessary. You will also have to ensure that the domain functional level is the same or higher than the forest functional level you intend to have.
Secondly, check and ensure whether replication is working properly in your forest, as it is a crucial functionality that you don’t want to be broken.
Finally, to ensure a seamless transition to a higher forest functional level, verify whether all your organization’s enterprise applications and services are compatible with the forest functional level you intend to have.
These steps will ensure a smooth upgrade to the higher functional level of choice, and you will not have any nasty surprises after the upgrade process.
Dependencies of Active Directory Functional Levels
Active Directory forest functional levels have the following dependencies:
- When all domain controllers (DCs) in a network are running one Windows Server version, the Active Directory Forest Functional level must be configured to support the same forest functional level. In order to provide advanced Active Directory features in a forest, an administrator must raise the forest functional level, which can only be done if the domain controllers are each running the same version of Windows Server.
- After the forest functional level is raised, domain controllers (DCs) running earlier versions of Windows Server cannot be added to the forest.
Raise domain or forest functional level first?
Forest functional level also dictates the minimum functional level at which all DCs in the forest should operate. Any DC that runs on a lower version of the Windows server will be demoted from the DC position. This restriction, however, is only applicable to DCs. Member servers and workstations in the forest will remain unaffected. So, the best practice is to raise the domain functional level first and then raise the forest functional level. Although, raising the forest functional level will automatically raise the domain functional level too.
Read how you can raise the domain functional level.
Accessible functionalities according to functional levels
A good practice before raising the forest functional level is to understand the functionalities that each functional level brings to the table so that you can take an informed decision. Each functional level carries over the functionalities of the previous one and adds additional functionalities on top. Some levels do not introduce any major functionalities, while others bring massive improvements. The availability of each function is what determines the functional level of an active directory forest. To help you understand better, here is a split-up of all functionalities that were introduced with each Windows Server version.
| FOREST FUNCTIONAL LEVEL | AVAILABLE FEATURES |
|---|---|
| Windows Server 2016 | Privileged Access Management (PAM) using Microsoft Identity Manager (MIM) |
| Windows Server 2012R2 | All available features of Windows Server 2012 FFL |
| Windows Server 2012 | All available features of Windows Server 2008R2 FFL |
| Windows Server 2008R2 | Active Directory Recycle BinAll available features of Windows Server 2003 FFL |
| Windows Server 2008 | All available features of Windows Server 2003 FFL |
| Windows Server 2003 | Forest trustDomain renameLinked-value replicationAbility to deploy a read-only DC (RODC)Improved Knowledge Consistency Checker (KCC) algorithms and scalabilityCreation of instances of the dynamic auxiliary class named dynamicObject in a domain directory partitionConversion of an inetOrgPerson object instance into a User object instance and the converseCreation of instances of new group types for role-based authorizationDeactivation and redefinition of attributes and classes in the schemaDomain-based DFS namespacesAll default AD DS features |
| Windows 2000 native | All default AD DS features |